Would you like to learn how to secure your Apache website from using Let's encrypt free HTTP certificate? In this tutorial, we are going to show you all the steps required to Secure Apache with Let's Encrypt on Ubuntu Linux
• Ubuntu version: 18.04
To illustrate the installation, we are going to use one of our domains named MINING-POOL.NINJA.
You will need to change the configuration files and replace our domain name MINING-POOL.NINJA by your domain name.
Hardware List:
The following section presents the list of equipment used to create this WordPress tutorial.
Every piece of hardware listed above can be found at Amazon website.
Apache Related Tutorial:
On this page, we offer quick access to a list of tutorials related to Apache.
1. Purchase a Domain Name
First, you need to access the GODADDY WEBSITE and create an account.
This account will be used to purchase a DNS domain.
In our example, we purchase the domain named MINING-POOL.NINJA.
Feel free to use any website to purchase a DNS domain.
GoDaddy is just my favorite choice.
2. Configure a DNS Entry
Now, you need to configure a DNS registry pointing to your Apache web server.
After purchasing a DNS domain, you need to create a DNS entry pointing your website address to the computer running Ubuntu Linux.
In our example, we created a DNS entry pointing the domain MINING-POOL.NINJA to the IP address 35.163.100.49.
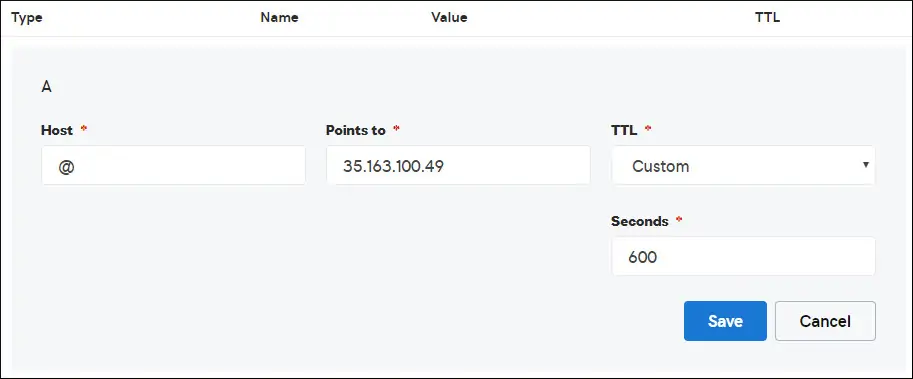
Use the following commands to test your DNS configuration on a computer running Linux.
# apt-get update
# apt-get install dnsutils
# nslookup mining-pool.ninja
Non-authoritative answer:
Name: mining-pool.ninja
Address: 35.163.100.49
The command above confirmed the domain is pointing to the IP address 35.163.100.49.
3. Install Apache Web server
The Let's Encrypt Certification authority requires the user to have a fully functional Apache web server.
We need to install the Apache web server and all the required software.
On the Linux console, use the following commands to install the required packages.
# apt-get update
# apt-get install apache2 php7.2 php7.2-mysql libapache2-mod-php7.2
# apt-get install openssl
Enable the Apache mod_rewrite and edit the apache2.conf file.
# a2enmod rewrite
# vi /etc/apache2/apache2.conf
At the end of the file, add the following lines.
<Directory /var/www/html>
AllowOverride All
</Directory>
Create an Apache Virtualhost configuration file to your website.
# vi /etc/apache2/sites-available/mining-pool.conf
Keep in mind that your Virtualhost file name and location may not be the same as mine.
As an example, here is the content of our file:
<VirtualHost *:80>
ServerAdmin nobody@care.com
DocumentRoot /websites/www
ServerName mining-pool.ninja
<Directory /websites/www/>
Options Indexes FollowSymLinks
AllowOverride All
Require all granted
</Directory>
ErrorLog /websites/logs/error.log
CustomLog /websites/logs/access.log combined
LogLevel error
</VirtualHost>
Create the list of required folders.
Set the correct file permission on all folders.
Keep in mind that your folder location may not be the same as mine.
# mkdir /websites
# cd /websites
# mkdir www logs
# chown www-data.www-data /websites -R
Enable your Apache Virtualhost configuration and restart the Apache service.
# a2ensite mining-pool.conf
# systemctl reload apache2
4. Configure the Free HTTPS Certificate on Apache
On the Linux console, use the following command to install the required packages.
# apt-get install software-properties-common
# add-apt-repository universe
# add-apt-repository ppa:certbot/certbot
# apt-get update
# apt-get install python-certbot-apache
The Certbot script requires the user to have a fully functional Apache web server.
We already finished our Apache Virtualhost installation and configuration.
Use the following command request and install the Apache free HTTPS certificate.
Keep in mind that your domain name should not be the same as mine.
# certbot --apache -d mining-pool.ninja
• Press (A) to Agree with the Terms of Service.
• Press (Y) to share your e-mail and receive Newsletters.
• Press (2) to automatically redirect your HTTP website to the HTTPS versions.
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator apache, Installer apache
Enter email address (used for urgent renewal and security notices) (Enter 'c' to
cancel): techexpert.tips@gmail.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree in order to register with the ACME server at
https://acme-v02.api.letsencrypt.org/directory
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(A)gree/(C)ancel: A
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing to share your email address with the Electronic Frontier
Foundation, a founding partner of the Let's Encrypt project and the non-profit
organization that develops Certbot? We'd like to send you email about our work
encrypting the web, EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for mining-pool.ninja
Enabled Apache rewrite module
Waiting for verification...
Cleaning up challenges
Created an SSL vhost at /etc/apache2/sites-available/mining-pool-le-ssl.conf
Enabled Apache socache_shmcb module
Enabled Apache ssl module
Deploying Certificate to VirtualHost /etc/apache2/sites-available/mining-pool-le-ssl.conf
Enabling available site: /etc/apache2/sites-available/mining-pool-le-ssl.conf
Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: No redirect - Make no further changes to the webserver configuration.
2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for
new sites, or if you're confident your site works on HTTPS. You can undo this
change by editing your web server's configuration.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2
Enabled Apache rewrite module
Redirecting vhost in /etc/apache2/sites-enabled/mining-pool.conf to ssl vhost in /etc/apache2/sites-available/mining-pool-le-ssl.conf
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Congratulations! You have successfully enabled https://mining-pool.ninja
You should test your configuration at:
https://www.ssllabs.com/ssltest/analyze.html?d=mining-pool.ninja
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/mining-pool.ninja/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/mining-pool.ninja/privkey.pem
Your cert will expire on 2019-03-19. To obtain a new or tweaked
version of this certificate in the future, simply run certbot again
with the "certonly" option. To non-interactively renew *all* of
your certificates, run "certbot renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
The system will automatically request the certificate and configure your Apache web server to redirect all HTTP access to the HTTPS version of your website.
In our example, the system created an HTTPS Virtualhost configuration file named mining-pool-le-ssl.conf
Here is the content of the HTTPS Virtualhost configuration file mining-pool-le-ssl.conf:
<IfModule mod_ssl.c>
<VirtualHost *:443>
ServerAdmin nobody@care.com
DocumentRoot /websites/www
ServerName mining-pool.ninja
<Directory /websites/www/>
Options Indexes FollowSymLinks
AllowOverride All
Require all granted
</Directory>
ErrorLog /websites/logs/error.log
CustomLog /websites/logs/access.log combined
LogLevel error
SSLCertificateFile /etc/letsencrypt/live/mining-pool.ninja/fullchain.pem
SSLCertificateKeyFile /etc/letsencrypt/live/mining-pool.ninja/privkey.pem
Include /etc/letsencrypt/options-ssl-apache.conf
</VirtualHost>
</IfModule>
The KEY file contains your Certificate private key and must be kept in a safe place all the time.
Here is the content of the KEY file: /etc/letsencrypt/live/mining-pool.ninja/privkey.pem
-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQCwGYFx4kcQmYC5
gJftnjZhWNVZkIL7wSMTFtFfIY37PNbVNeJ11HoudX8HWout8qXOxBvHE8oUtzrO
/956cCVNsdY+eXZVVwUhjeSRT9wH2vUh3vVw6mi0TRy1KZJGo+hFeUS7zGb0/IwV
MofsEE3rAM1s9RoNOzH6Q/S7OiXFH4OhjbORcv0mBBDjbUgIB+PPoSdCj98yHjZN
vyVEvU9xZLQZxDfFMJr9lNAOR0AIOaALkXaMu1zC5+G1Z2x+W9xSI4JMegiKoHhI
/Xt3A3lCyT81GGc3RrmlighZZVstr0FK4XotcJe5YLsBn1xIukyUrWnJHGRz8MmC
26ShYRLLAgMBAAECggEAdpK19ljGQQcbBczwf67oLuQBxCzqBVomo9PZZpTRZTmx
7h46Pdyz6FR1FB6DrryTqIWjrohEqW42yuq+gvLAK3BzMd3XL99INS+1l6KOJTvp
ksTtvvoXRlAl5FX5iFcVLrJY9ZrMOGlUaXF81BamYHZJ2/OtdvtEy562Str8U52m
GTkgfpWnaLc66T05zViNwiAb5yg0v9Xb9YOEgLY8VdqYppUnJNzYs7utiDGbOjPa
OCZ5oLTl1b9l6sNw7RhhOmq/jPOur4Keg124fyleULi2Uln52waLWeI8fWI/AHmP
UQQkC3athEOKr0f1Zk9ZRxYJq5FYGPTElqQdbltEAQKBgQDiqSp4XM0tfFJwZIkH
ooEcPw+to4T0333K4mipx+YxlELCHvIXW2xIxlejyhgnVIQWX6qS0F7VUGnVuSKz
hB0zfcd89MYcqGyQSEdc9kZB+Twb9Hzd3fTXu7hKjXoz9+UKfcOXfQdILGnDqyG8
zCF//aNocRvxaO9E1cZ+1irlcQKBgQDG5OZUr8kMYI8Tl0GcmWZSFZfMYBYT3CAq
YPHmNQcHhENGz6v9jBZjkeZJBLMRZLlRWjcrWhKbEEHsjZJYiJP4u2n6n57Il9h9
OVqfK7RR3k1r9bMKzhYRnu1FsEPpMKKUrLPDChthxduXEPPZgoKGSYmhLAiYqyPg
USOyZzFt+wKBgQCmfjSgLSrZ2pSD0pWFciz8nqXZml+zr+cq/Jx8+kVw7cML7MdP
uOwVmPwPaAfN/Br6hFM7fKvsbSEQyOlgjA8XH7FFbFeJ/X2hjjY9Zvm8xGMO9cwy
/TM4tL9uo/W77r/jsPXXdRPARD98Z1xk3l1NMvaxZURtU/NN0On5iUABQQKBgGIu
FiER0R3iAF68WLAT7TVx4UgK2nsdO2eQCXkJDhpAyPEIjK8RWu/10oaS4k4guXYW
IYut3+dZpCFAVVCMwvaSlSMZbkk4464VBM3zxgRvxyoW1DXuO2ihWiD/fNZ8opTf
l7EcqR2fjOFKhgUF7qaZYG4GDYxHVuNhSkzDsdvHAoGBAIfDk7fLsG/BYROxJpzN
b1CoG8DE+DKYTWwMWW45rDF0ImbC6H3fg876CeZ3YKGWqt9qkha7gnGGVRRufP15
O7ZEXebZXeDYafXSNcnqSe7FSNtVr1eFlTWmL8OiWQuaqxjs/VogdWfhkEGPISVF
AOM3I6XSGx4NxW2RgYmvQZ4O
-----END PRIVATE KEY-----
The system automatically changed your original Apache Virtualhost configuration file to redirect all HTTP requests to the HTTPS version.
Here is the content of the updated original HTTP Virtualhost configuration file mining-pool.conf:
ServerAdmin nobody@care.com
DocumentRoot /websites/www
ServerName mining-pool.ninja
Options Indexes FollowSymLinks
AllowOverride All
Require all granted
ErrorLog /websites/logs/error.log
CustomLog /websites/logs/access.log combined
LogLevel error
RewriteEngine on
RewriteCond % =mining-pool.ninja
RewriteRule ^ https://%% [END,NE,R=permanent]
5. Test your Apache HTTPS Website
To test your installation, open your browser and enter your website HTTP address.
In our example, the following URL was entered in the Browser:
• http://mining-pool.ninja
Instead of the HTTP version, the HTTPS version of your website should be presented.
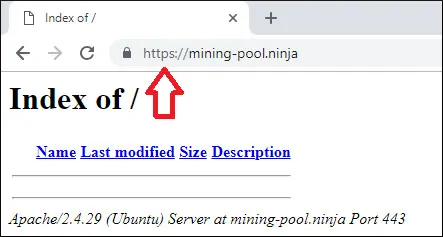
Congratulations, your Apache configuration is now using the LET'S ENCRYPT free HTTPS certificate.
6. Renew the Apache HTTPS Certificate
You need to be aware that Let's Encrypt's certificates are only valid for ninety days.
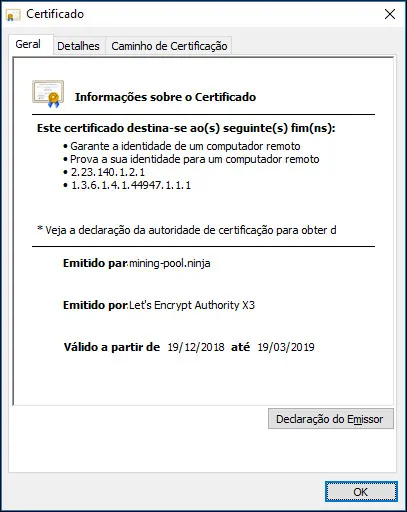
The System creates a scheduled task to automatically renew any certificate that is within thirty days of expiration.
The scheduled task name is certbot and it is located inside the directory /etc/cron.d.
Here is the content of the /etc/cron.d/certbot file:
# /etc/cron.d/certbot: crontab entries for the certbot package
#
# Upstream recommends attempting renewal twice a day
#
# Eventually, this will be an opportunity to validate certificates
# haven't been revoked, etc. Renewal will only occur if expiration
# is within 30 days.
#
# Important Note! This cronjob will NOT be executed if you are
# running systemd as your init system. If you are running systemd,
# the cronjob.timer function takes precedence over this cronjob. For
# more details, see the systemd.timer manpage, or use systemctl show
# certbot.timer.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
0 */12 * * * root test -x /usr/bin/certbot -a \! -d /run/systemd/system && perl -e 'sleep int(rand(43200))' && certbot -q renew
Use the following command to simulate the process of certificate renew.
# certbot renew --dry-run
If everything is working, you should see the following messages:
Saving debug log to /var/log/letsencrypt/letsencrypt.log
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Processing /etc/letsencrypt/renewal/mining-pool.ninja.conf
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Cert not due for renewal, but simulating renewal for dry run
Plugins selected: Authenticator apache, Installer apache
Renewing an existing certificate
Performing the following challenges:
http-01 challenge for mining-pool.ninja
Waiting for verification...
Cleaning up challenges
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
new certificate deployed with reload of apache server; fullchain is
/etc/letsencrypt/live/mining-pool.ninja/fullchain.pem
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
** DRY RUN: simulating 'certbot renew' close to cert expiry
** (The test certificates below have not been saved.)
Congratulations, all renewals succeeded. The following certs have been renewed:
/etc/letsencrypt/live/mining-pool.ninja/fullchain.pem (success)
** DRY RUN: simulating 'certbot renew' close to cert expiry
** (The test certificates above have not been saved.)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
IMPORTANT NOTES:
- Your account credentials have been saved in your Certbot
configuration directory at /etc/letsencrypt. You should make a
secure backup of this folder now. This configuration directory will
also contain certificates and private keys obtained by Certbot so
making regular backups of this folder is ideal.
