Would you like to learn how to configure Cacti LDAP authentication on Active directory? In this tutorial, we are going to show you how to authenticate Cacti users using the Microsoft Windows database Active directory and the LDAP protocol.
• Ubuntu 19.04
• Cacti 1.2.3
What is Cacti?
Cacti is an open-source platform for data monitoring that is completely PHP driven.
On the Web interface, users are able to use Cacti as a frontend to RRDtool, create Graphs and populate them with data stored in MySQL.
Cacti also has SNMP support for users to create graphs in order to perform network monitor.
Cacti Playlist:
On this page, we offer quick access to a list of videos related to Cacti installation.
Don't forget to subscribe to our youtube channel named FKIT.
Cacti Tutorial:
On this page, we offer quick access to a list of Cacti tutorials
Tutorial - Windows Domain Controller Firewall
First, we need to create a Firewall rule on the Windows domain controller.
This firewall rule will allow the Cacti server to query the Active Directory database.
On the domain controller, open the application named Windows Firewall with Advanced Security
Create a new Inbound firewall rule.
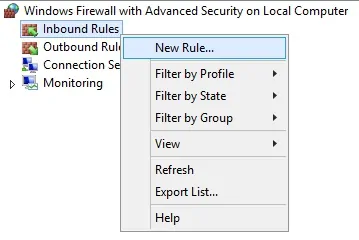
Select the PORT option.
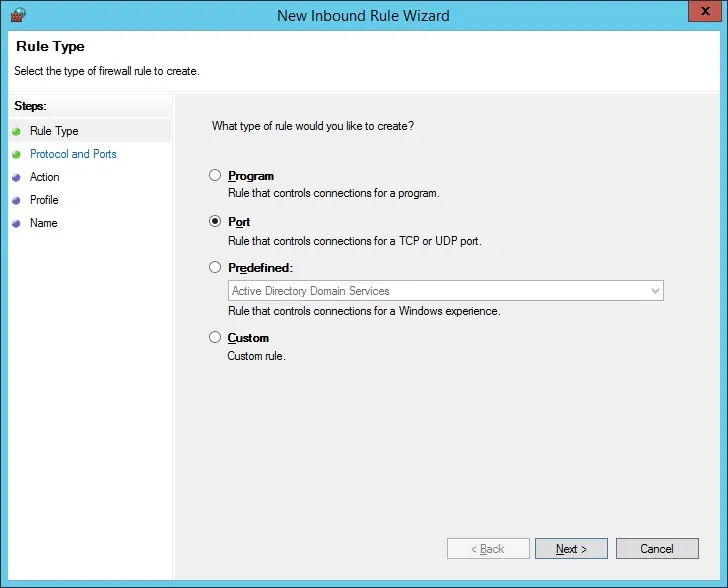
Select the TCP option.
Select the Specific local ports option.
Enter the TCP port 389.
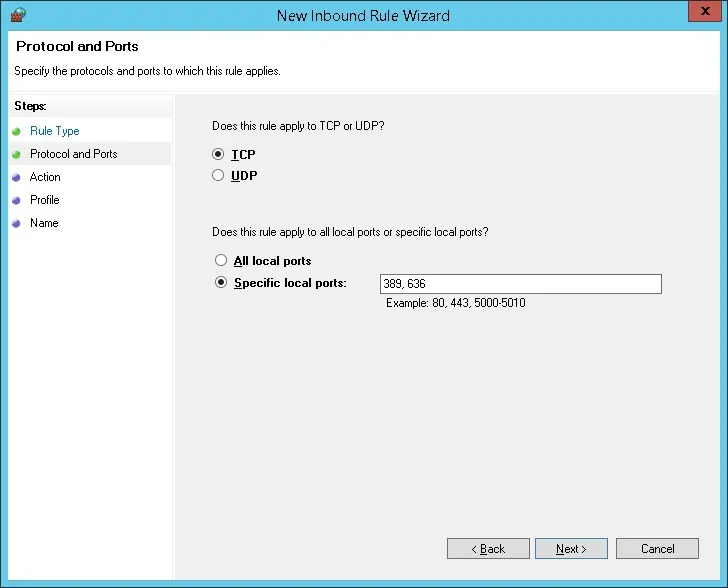
Select the Allow the connection option.
Check the DOMAIN option.
Check the PRIVATE option.
Check the PUBLIC option.
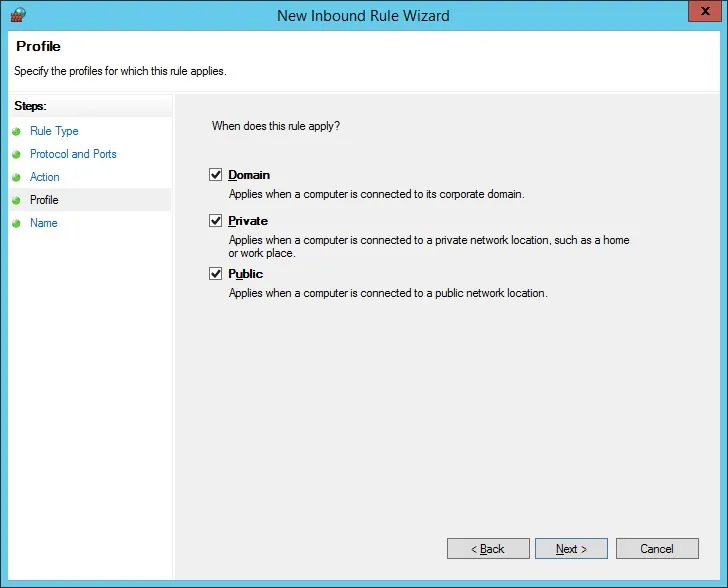
Enter a description to the firewall rule.
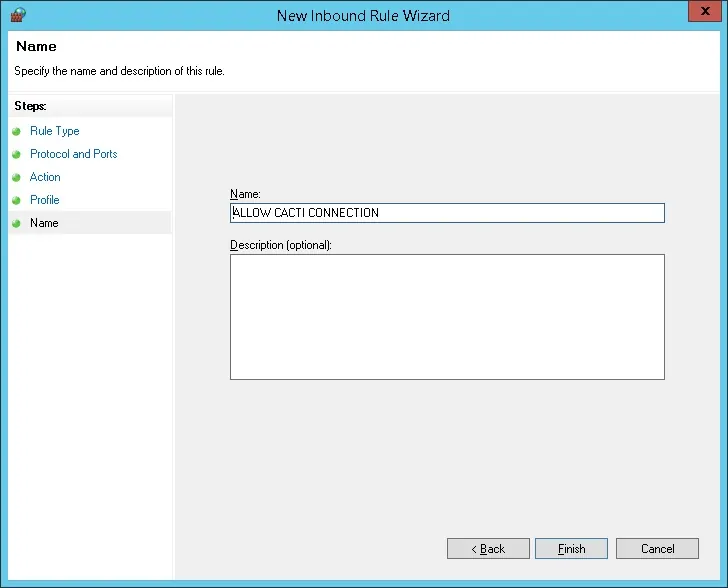
Congratulations, you have created the required firewall rule.
This rule will allow Cacti to query the Active Directory database.
Tutorial - Windows Domain Account Creation
Next, we need to create at least 2 accounts on the Active directory database.
The ADMIN account will be used to login on the Cacti web interface.
Important! The local Admin account will stop working after enabling LDAP.
The Cacti account will be used to query the Active Directory database.
On the domain controller, open the application named: Active Directory Users and Computers
Create a new account inside the Users container.
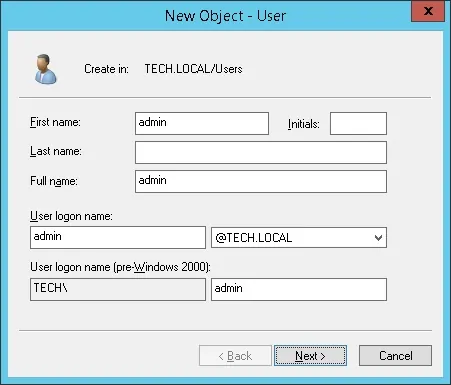
Create a new account named: admin
Password configured to the Admin user: 123qwe.
This account will be used to authenticate as admin on the Cacti web interface.
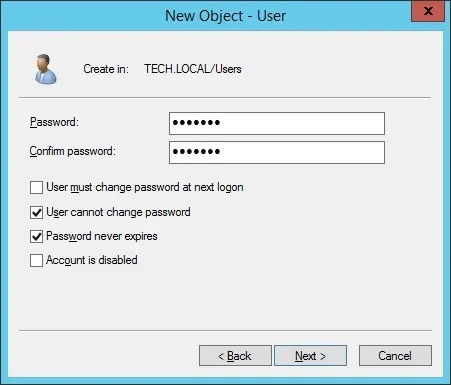
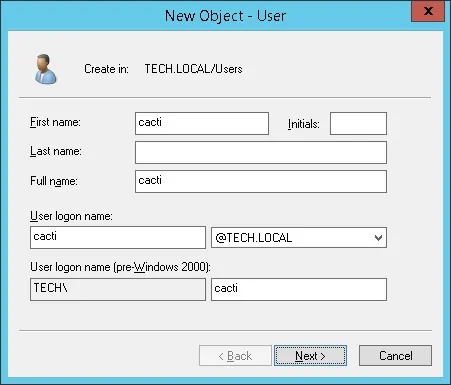
Create a new account named: Cacti
Password configured to the Cacti user: 123qwe.
This account will be used to show that our Active Directory configuration is working.
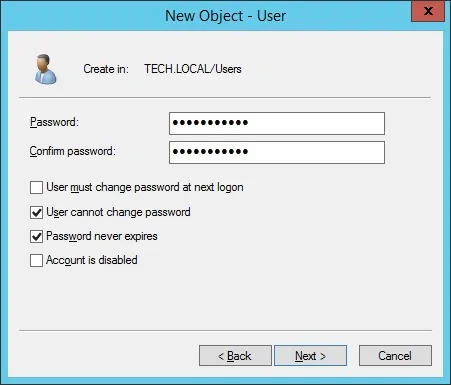
Congratulations, you have created the required Active Directory accounts.
Tutorial - Cacti LDAP Authentication on Active Directory
Before we start, let's create a backup of your database.
Use the following commands to create a Cacti database backup.
You will have to enter the Cacti mysql user password.
# mkdir /backup
# cd /backup
# mysqldump -u root -p cacti > cacti.sql
Make sure that you have the PHP LDAP module installed and restart the Apache webserver.
# apt-get install php-ldap
# service apache2 restart
You have successfully installed the required packages.
Tutorial - Cacti LDAP Authentication on Active Directory
Open your browser and enter the IP address of your web server plus /cacti.
In our example, the following URL was entered in the Browser:
• http://192.168.0.10/cacti
On the login screen, use the default username and default password.
• Default Username: admin
• Default Password: admin
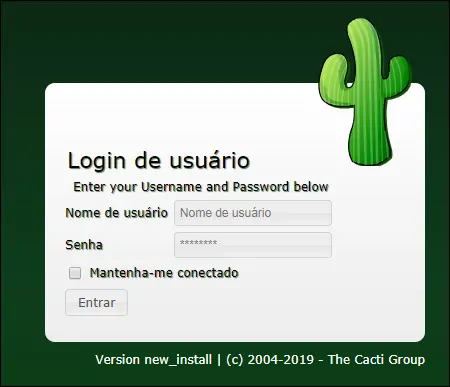
After a successful login, you will be sent to the Cacti Dashboard.
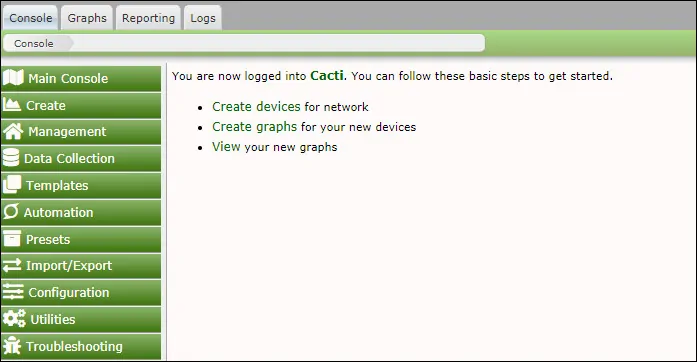
On the Cacti dashboard screen, access the Configuration menu and select the Users option.
Access the properties of the Guest user account, enable the Guest user account and set a password.
Click on the Save button.
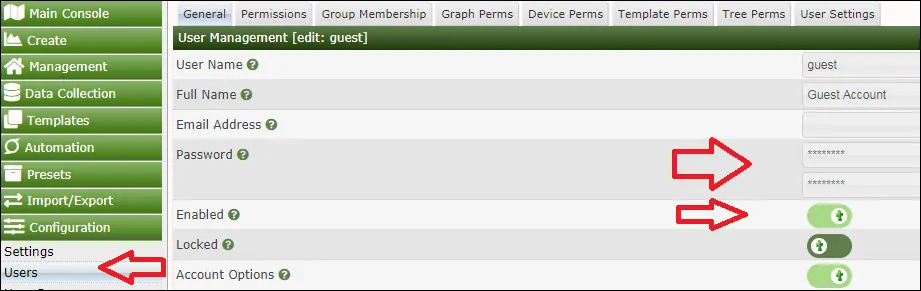
On the Cacti dashboard screen, access the Configuration menu and select the Settings option.
Access the Authentication tab and perform the following configuration:
General:
Authentication Method - LDAP Authentication
Special Users:
• Primary Admin - Admin
• Guest User - Guest
• User Template - Admin
LDAP General Settings:
• Server - IP address of Active Directory Domain controller
• Port Standard - 389
• Port SSL - 636
• Protocol Version - Version 3
• Encryption - None
• Referrals - Disabled
• Mode - No searching
• Distinguished Name (DN) - @tech.local
• Require Group Membership - No
You need to change the IP address to your domain controller IP.
You need to change the TECH.LOCAL domain information to reflect your Network environment.
Every time an Active directory user login the Web interface it will copy all user permissions from the ADMIN account.
If you don't want this configuration change the User Template configuration from Admin to Guest.
You may change the permission for each user on the user account properties.
To access the user account properties access the Configuration menu and select the Users option.
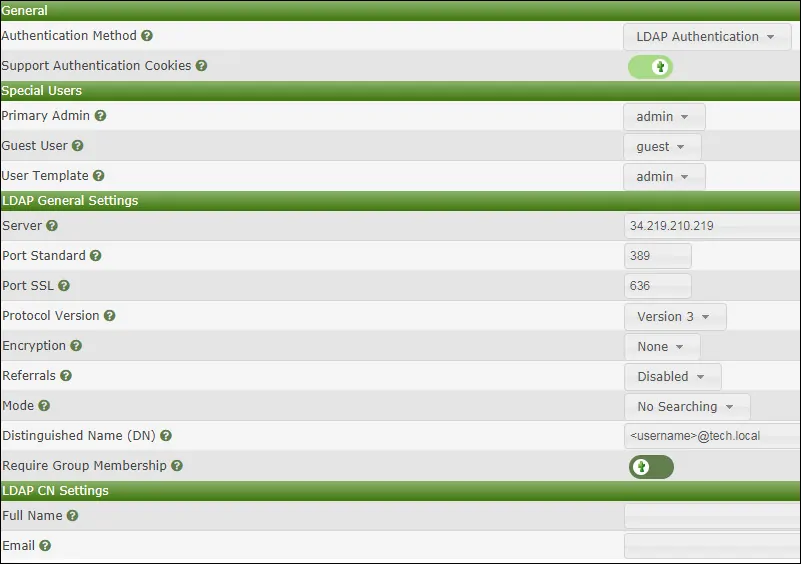
After saving your configuration, you should log off the Cacti web interface.
Try to login using the admin user and the password from the Active Directory database.
On the login screen, use the admin user, select the LDAP authentication and use the password from the Active Directory database.
• Username: Admin
• Password: Enter the Active directory password.
After a successful login, the Cacti dashboard will be presented.

Now, it is time to test a regular user login, you should log off the Cacti web interface.
Try to login using the Cacti user and the password from the Active Directory database.
On the login screen, use the Cacti user, select the LDAP authentication and use the password from the Active Directory database.
• Username: cacti
• Password: Enter the Active directory password.
After a successful login, the Cacti dashboard will be presented.
Congratulations! You have configured the Cacti LDAP authentication on Active Directory using LDAP.
In order to authenticate a user against Active directory, the user account must also exist in the Cacti server user database.

Leave A Comment
You must be logged in to post a comment.