Learn about XOR encryption in Python, a fundamental technique for data security. This article provides practical examples and insights, emphasizing its role in strengthening encryption protocols and ensuring data integrity.
Equipment list
Here you can find the list of equipment used to create this tutorial.
This link will also show the software list used to create this tutorial.
Related tutorial - Python
On this page, we offer quick access to a list of tutorials related to Python.
What is XOR?
XOR, short for exclusive or, is a logical operation that outputs true only when the number of true inputs is odd. In digital electronics, XOR is a fundamental logic gate that takes two binary inputs and produces an output that is true only when the inputs differ.
Is XOR used in encryption?
Yes, XOR is indeed used in some encryption algorithms and protocols, often as a component of more complex cryptographic techniques. While XOR alone is not considered a secure encryption method, it can be used in combination with other operations to provide a certain level of data protection.
XOR can be employed in stream ciphers, where it is used to combine the plaintext with a keystream. This process helps to ensure that the ciphertext produced is dependent on both the plaintext and the key. However, it is important to note that XOR by itself does not provide adequate security for sensitive data.
How do you encrypt with XOR?
To encrypt with XOR, you perform the XOR operation between the binary representation of the plaintext and a binary key of the same length. This involves comparing each bit of the plaintext with the corresponding bit of the key, and if the bits are different, the result is 1; if they are the same, the result is 0. The resulting binary sequence is then often converted back to a human-readable form, such as ASCII characters. XOR encryption is a simple and reversible process, but it is not considered secure on its own and is often used as a component of more complex encryption algorithms.
Tutorial Python - Using XOR Encryption
Create a function to encrypt using XOR.
Create a text and a key.
Encrypt the text using XOR.
Here is the command output.
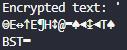
It is normal for encrypted output to take up several lines, especially if dealing with special characters or non-printable characters. The output may look strange or unreadable because it represents numeric values resulting from the XOR operation between the ASCII values of the text and key characters.
Create a function to decrypt using XOR.
Decrypt the cipher text using XOR.
Here is the command output.
Here is the complete Python script.
Python - Encoding a file using XOR encryption
Encode a file using XOR encryption.
Decode a file using XOR encryption.
Here is the complete Python script.
Conclusion
Coding with Python's XOR encryption offers a simple yet effective method for data security. Explore practical implementation and insights to fortify data protection in your projects.
