Would you like to learn how to use a group policy to enable the FilterAdministratorToken protection? In this tutorial, we will show you how to deny the built-in local administrator account to do remote administration tasks.
• Windows 2012 R2
• Windows 2016
• Windows 2019
• Windows 2022
• Windows 10
• Windows 11
Equipment list
Here you can find the list of equipment used to create this tutorial.
This link will also show the software list used to create this tutorial.
Windows Related Tutorial:
On this page, we offer quick access to a list of tutorials related to Windows.
Tutorial GPO – Enable FilterAdministratorToken
On the domain controller, open the group policy management tool.

Create a new group policy.
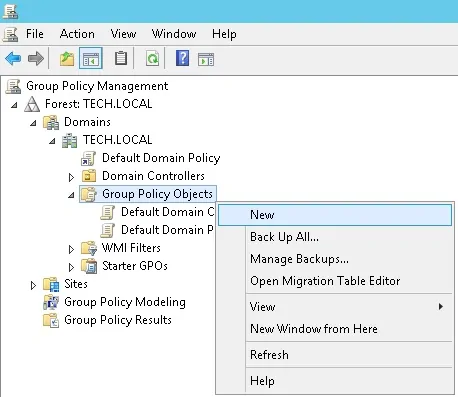
Enter a name for the new group policy.
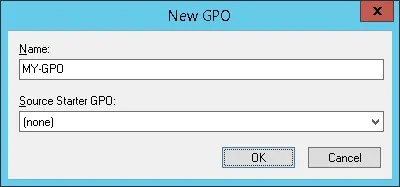
In our example, the new GPO was named: MY-GPO.
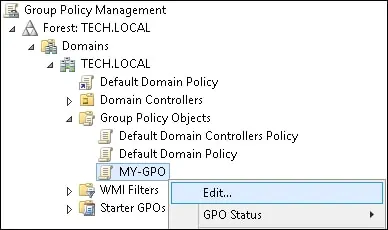
On the Group Policy Management screen, expand the folder named Group Policy Objects.
Right-click your new Group Policy Object and select the Edit option.
On the group policy editor screen, expand the Computer configuration folder and locate the following item.
Right-click on the Registry option and create a Registry entry.
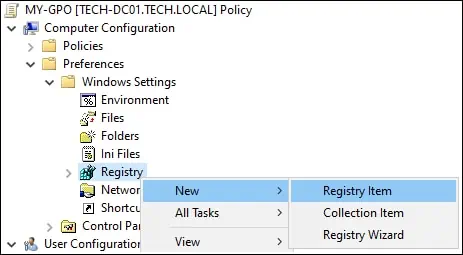
On the registry screen, perform the following configuration.
Click on the OK button.
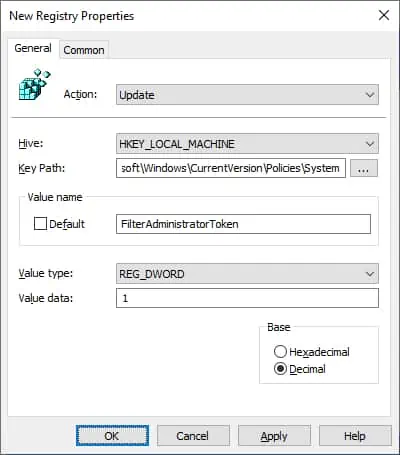
To save the group policy configuration, you need to close the Group Policy editor.
Congratulations! You have finished the GPO creation.
Tutorial GPO – Enable FilterAdministratorToken
On the Group policy management screen, you need to right-click the Organizational Unit desired and select the option to link an existent GPO.
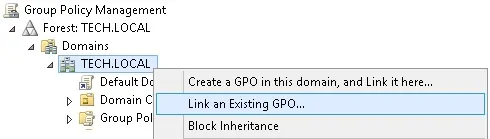
In our example, we are going to link the group policy named MY-GPO to the root of the domain.
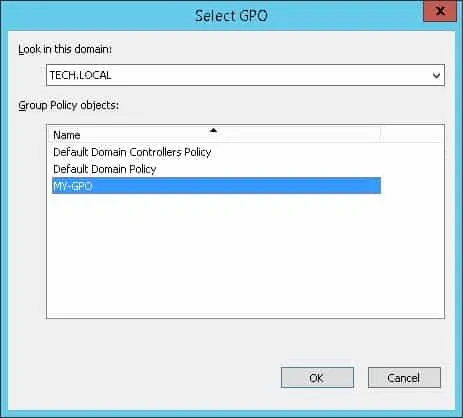
After applying the GPO you need to wait for 10 or 20 minutes.
During this time the GPO will be replicated to other domain controllers.
On a remote computer, verify if the registry key was created.
In our example, we used a GPO to enable the FilterAdministratorToken protection and deny the built-in local administrator account to do remote administration tasks.
