Would you like to learn how to configure an Nginx server to use LDAP authentication on the Active Directory? In this tutorial, we are going to show you how to authenticate the Nginx service on the Active Directory using the LDAP protocol on a computer running Ubuntu Linux.
• Ubuntu 20
• Ubuntu 19
• Ubuntu 18
• Nginx 1.18.0
• Windows 2012 R2
Equipment list
The following section presents the list of equipment used to create this tutorial.
As an Amazon Associate, I earn from qualifying purchases.
Nginx - Related Tutorial:
On this page, we offer quick access to a list of tutorials related to Nginx.
Tutorial - Windows Domain Controller Firewall
• IP - 192.168.15.10
• Operacional System - WINDOWS 2012 R2
• Hostname - TECH-DC01
First, we need to create a Firewall rule on the Windows domain controller.
This firewall rule will allow the Nginx server to query the Active Directory database.
On the domain controller, open the application named Windows Firewall with Advanced Security
Create a new Inbound firewall rule.
Select the PORT option.
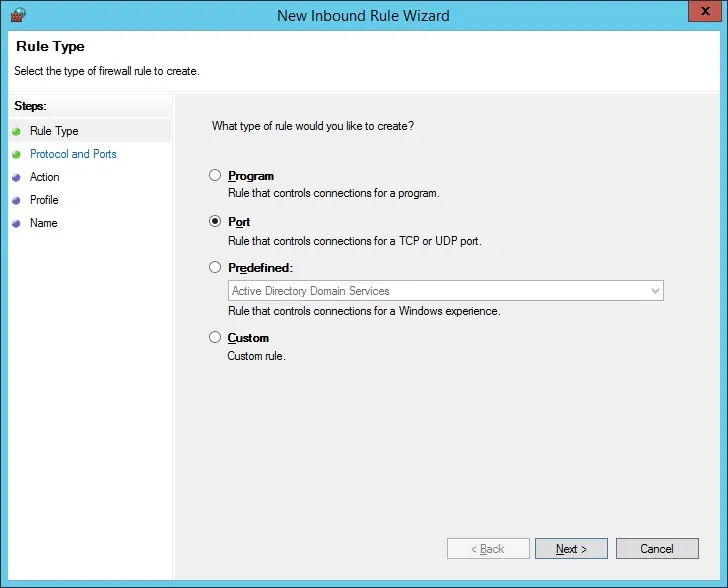
Select the TCP option.
Select the Specific local ports option.
Enter the TCP port 389.
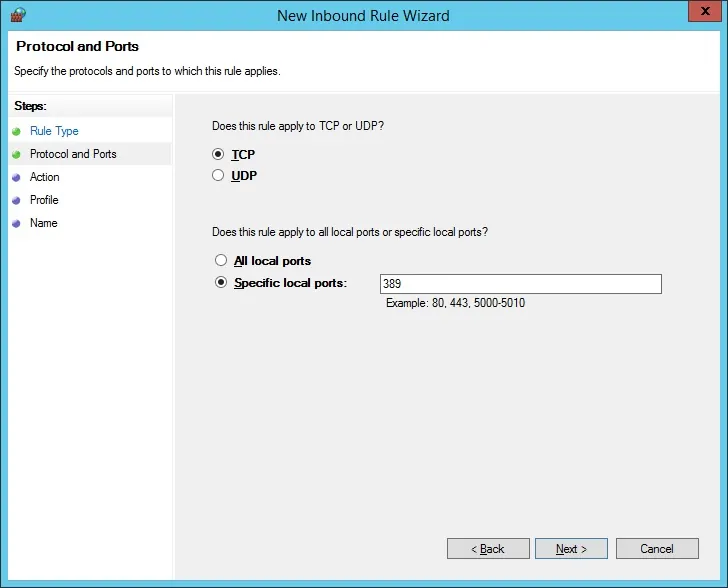
Select the Allow the connection option.
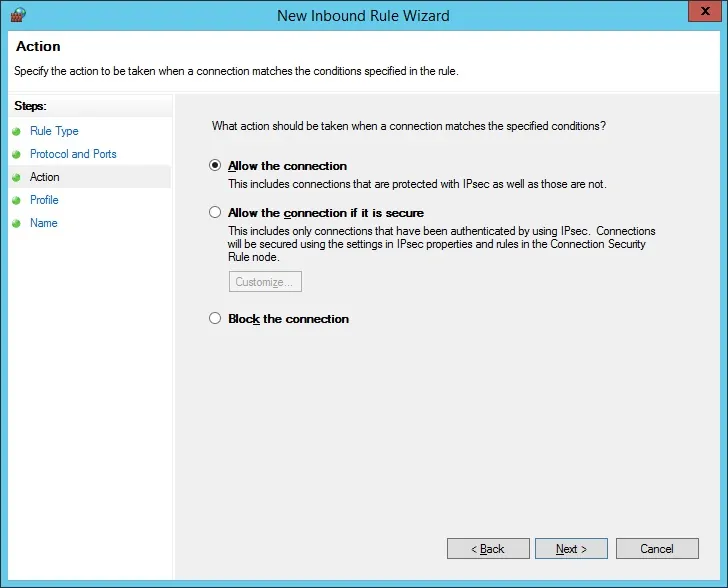
Check the DOMAIN option.
Check the PRIVATE option.
Check the PUBLIC option.
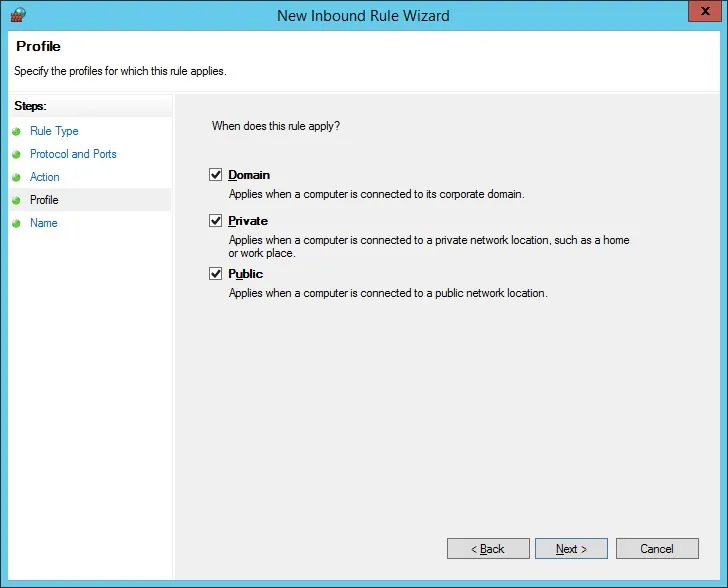
Enter a description to the firewall rule.
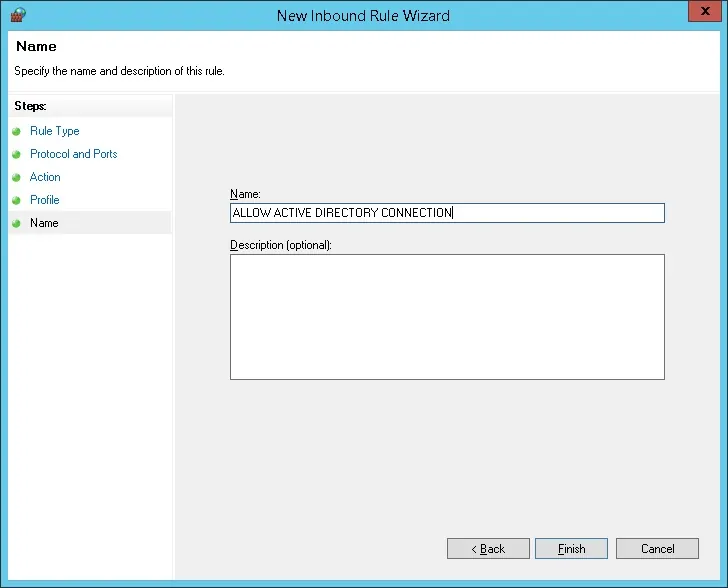
Congratulations, you have created the required firewall rule.
This rule will allow the Nginx server to query the Active Directory database.
Tutorial - Windows Domain Account Creation
Next, we need to create at least 2 accounts on the Active Directory database.
The ADMIN account will be used to login to the Nginx server.
The BIND account will be used to query the Active Directory database.
On the domain controller, open the application named: Active Directory Users and Computers
Create a new account inside the Users container.
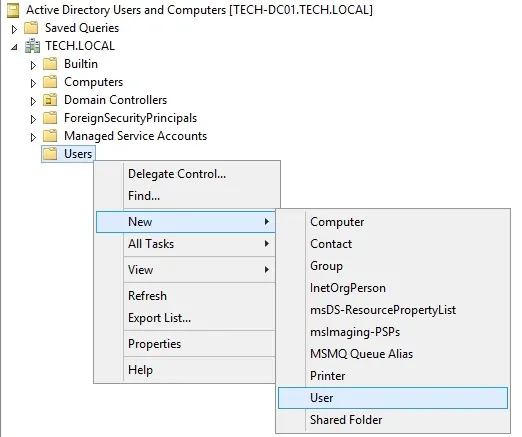
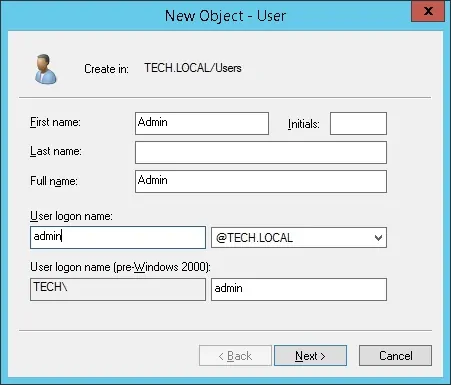
Create a new account named: admin
Password configured to the ADMIN user: 123qwe..
This account will be used to authenticate on the Nginx web interface.
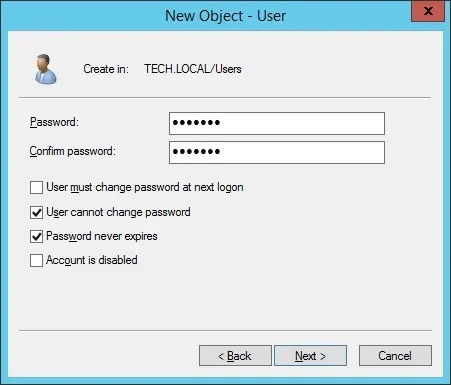
Create a new account named: bind
Password configured to the BIND user: kamisama123..
This account will be used to query the passwords stored on the Active Directory database.
Congratulations, you have created the required Active Directory accounts.
Tutorial Nginx - LDAP authentication
• IP - 192.168.15.20
• Operational System - Ubuntu 20.04
• Hostname - NGINX
Install the Nginx server.
Edit the Nginx configuration file for the default website.
Here is the file before our configuration.
Here is the file after our configuration.
In our example, the Nginx configuration requires user authentication to access any part of the website.
Nginx does not have native LDAP authentication.
The authentication information sent to Nginx will be forwarded to the web server 192.168.15.30.
If the remote server validates the user authentication, Nginx will authorize the user access.
Restart the Nginx service.
You have finished the Nginx required configuration.
Nginx - Using Apache as the authentication proxy
• IP - 192.168.15.30
• Operational System - Ubuntu 20.04
• Hostname - APACHE
Now, we need to configure the remote server that will be responsible for the credential validation.
In our example, we are going to use an Apache server to validate the user credential on the LDAP server.
Install the Apache server and the required LDAP authentication module.
Enable the Apache2 LDAP authentication module.
Create a directory named AUTH and give the user named www-data permission over this directory.
Configure the Apache server to request the LDAP authentication to users trying to access this directory.
Edit the Apache configuration file for the default website.
Here is the configuration file before our configuration.
Here is the file after our configuration.
The Apache server was configured to request password authentication to access the directory named AUTH.
The Apache web server was configured to authenticate user accounts using the LDAP server 192.168.15.10.
The Apache web server was configured to use the Active Directory domain: TECH.LOCAL.
Restart the Apache service.
Congratulations! You successfully configured the Apache authentication.
Nginx - LDAP authentication test
Open your browser and enter the IP address of your Nginx web server.
In our example, the following URL was entered in the Browser:
• http://192.168.15.20
The Nginx server will require you to perform the user authentication.
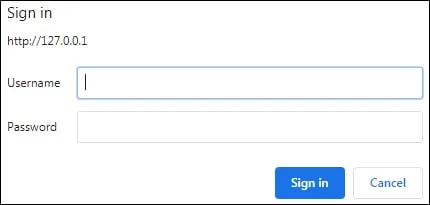
After a successful login, you will be authorized to access the website.
Congratulations! You configured the LDAP authentication on the Nginx server to use the Active Directory.
