Would you like to learn how to configure a Cisco Switch SSH authentication on Active directory via Radius using the command-line? In this tutorial, we are going to show you all the steps required to configure SSH authentication via Microsoft Active Directory on a Cisco Switch 2960 using the command-line.
In our example, the Windows domain controller has the IP address 192.168.100.10.
Cisco Switch Playlist:
On this page, we offer quick access to a list of videos related to Cisco Switch.
Don't forget to subscribe to our youtube channel named FKIT.
Cisco Switch Related Tutorial:
On this page, we offer quick access to a list of tutorials related to Cisco Switch.
Tutorial - Cisco SSH Authentication on Active Directory
First, you need to access the console of your Cisco Switch.
In our example, we are going to use an Opensource software named Putty and a computer running Windows.
The Putty software is available on the putty.org website.
After finishing the download, run the software and wait for the following screen.
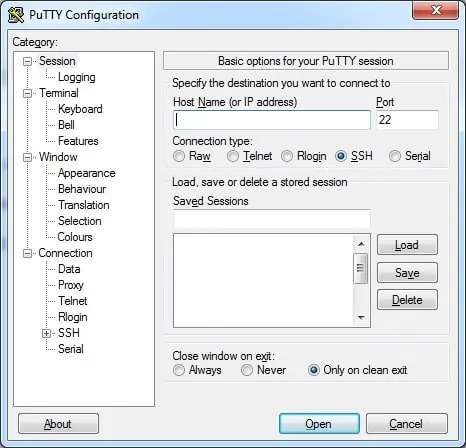
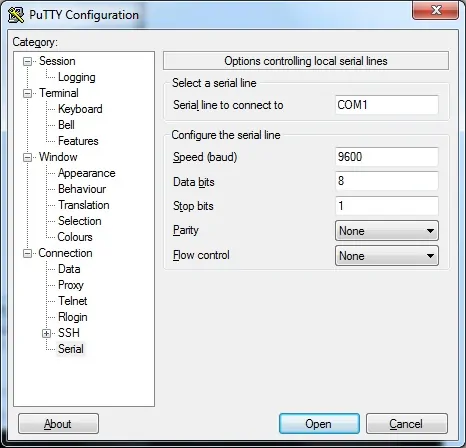
To access the console of a Cisco Switch model 2960 or 3750, you will need to select the Serial Connection category and use the following options:
• Connection type: Serial
• Serial line: COM1
• Speed: 9600
If COM1 does not work you will need to try to use COM2, COM3, COM4 or the next.
Using either the console, telnet or ssh, connect to the command-line of your switch and log in with a user who has administrative privileges.
On the prompt screen, enter the administrative login information.
After a successful login, the console command-line will be displayed.
Switch>
Use the enable command to enter the privilege mode.
Switch> enable
Use the configure terminal command to enter the configuration mode.
Switch# configure terminal
First, you need to install and configure the Radius on a Windows server.
The video above will teach you the step by step procedure required to configure the Radius server.
After finishing the Radius server configuration you may continue to read the tutorial.
Configure the Cisco switch to authenticate using the Radius server.
Switch(config)# aaa new-model
Switch(config)# aaa authentication login default group radius local
Switch(config)# aaa authorization exec default group radius local
Switch(config)# radius-server host 192.168.100.10
Switch(config)# radius-server key kamisama123@
In our example, we configured the Cisco Switch to authenticate and authorize user session using the Radius server.
The radius server is authenticating the user accounts on the Active Directory domain.
In our example, the IP address of the Radius server is 192.168.100.10.
In our example, Authentication key to the radius server is kamisama123@.
Now, use the following command to create the needed SSH encryption keys:
Switch(config)# crypto key generate rsa
Switch(config)# ip ssh version 2
If the system asks for a key size, you should inform the highest number available for your switch.
On my Switch, the maximum value was: 4096
You should also enable the SSH version 2 which is more secure and has a lot of cool features.
Configure the virtual terminals to allow SSH remote access.
Switch(config)# line vty 0 15
Switch(config)# login authentication default
Switch(config)# transport input ssh
Switch(config)# exit
Don’t forget to save your switch configuration.
Switch# copy running-config startup-config
You have successfully enabled the Cisco SSH remote access feature.
You have successfully configured the remote terminals to accept remote connections.
You have successfully configured the Radius authentication on a Cisco switch.
