Would you like to learn how to configure the Zabbix Active directory authentication using LDAP over SSL? In this tutorial, we are going to show you how to authenticate Zabbix users on the Active Directory database using the LDAPS protocol for an encrypted connection.
• Zabbix 4.2.6
• Windows 2012 R2
Hardware List:
The following section presents the list of equipment used to create this Zabbix tutorial.
Every piece of hardware listed above can be found at Amazon website.
Zabbix Playlist:
On this page, we offer quick access to a list of videos related to Zabbix installation.
Don't forget to subscribe to our youtube channel named FKIT.
Zabbix Related Tutorial:
On this page, we offer quick access to a list of tutorials related to Zabbix installation.
Tutorial - Active Directory Installation on Windows
• IP - 192.168.15.10.
• Operacional System - Windows 2012 R2
• Hostname - TECH-DC01
• Active Directory Domain: TECH.LOCAL
If you already have an Active Directory domain, you may skip this part of the tutorial.
Open the Server Manager application.
Access the Manage menu and click on Add roles and features.
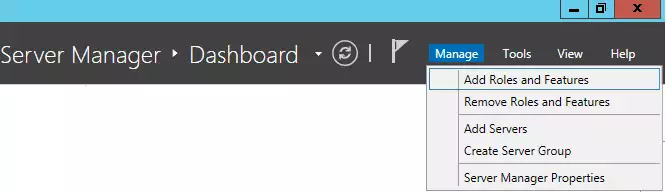
Access the Server role screen, select the Active Directory Domain Service and click on the Next button.
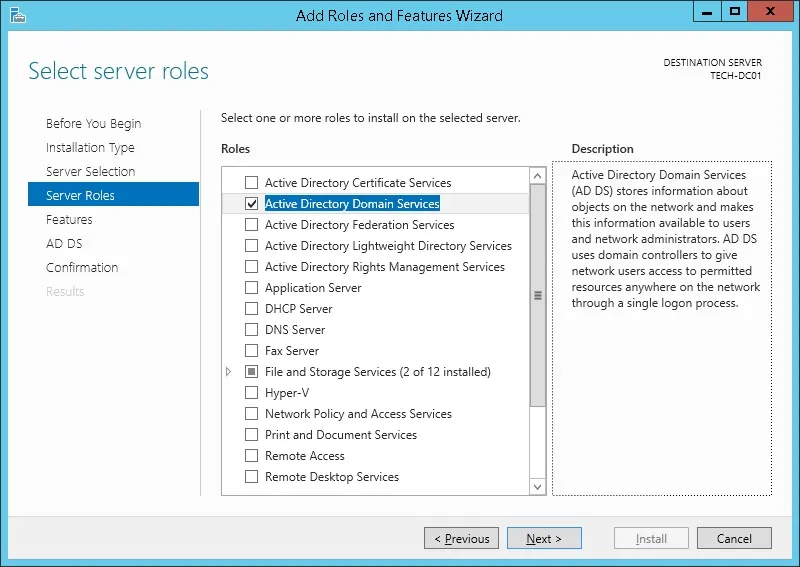
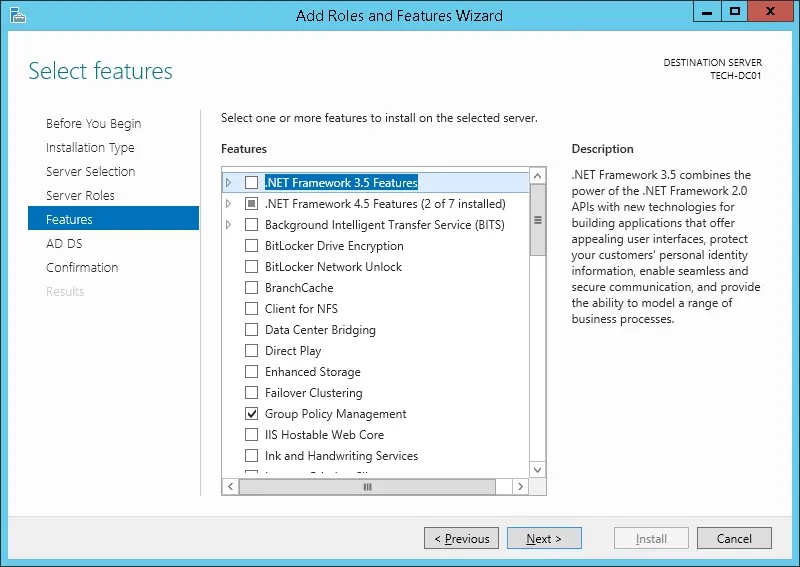
On the following screen, click on the Add features button.
Keep clicking on the Next button until you reach the last screen.
On the confirmation screen, click on the Install button.
Wait the Active directory installation to finish.
Open the Server Manager application.
Click on the yellow flag menu and select the option to promote this server to a domain controller
Select the option to Add a new forest and enter a root domain name.
In our example, we created a new domain named: TECH.LOCAL.
Enter a password to secure the Active Directory restoration.
On the DNS options screen, click on the Next button.
Verify the Netbios name assigned to your domain and click on the Next button.
Click on the Next button.
Review your configuration options and click on the Next button.
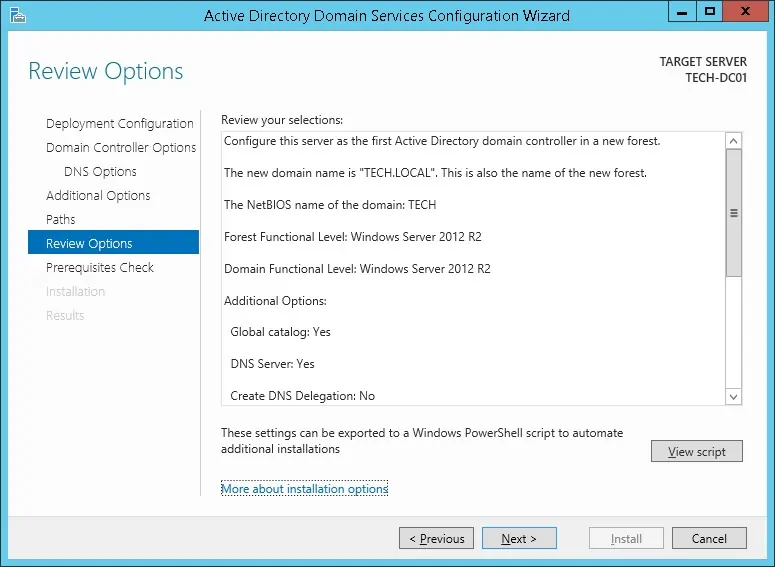
On the Prerequisites Check screen, click on the Install button.
Wait the Active Directory Configuration to finish.
After finishing the Active directory installation, the computer will restart automatically
You have finished the Active directory configuration on Windows server.
Zabbix - Testing the LDAP over SSL communication
We need to test if your domain controller is offering the LDAP over SSL service on port 636.
On the domain controller, access the start menu and search for the LDP application.
First, let's test if your domain controller is offering the LDAP service on port 389.
Access the Connection menu and select the Connect option.
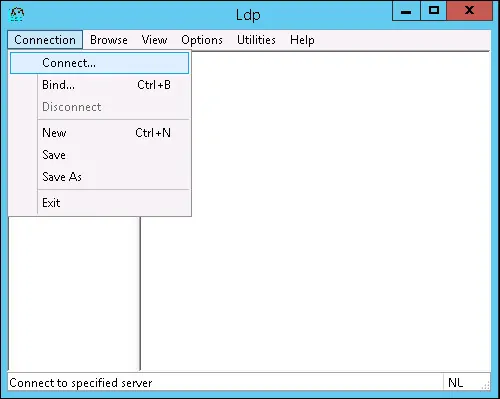
Try to connect to the localhost using the TCP port 389.
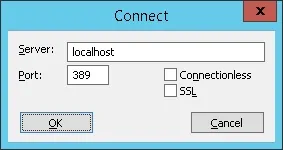
You should be able to connect to the LDAP service on the localhost port 389.
Now, we need to test if your domain controller is offering the LDAP over SSL service on port 636.
Open a new LDP application Window and try to connect to the localhost using the TCP port 636.
Select the SSL checkbox and click on the Ok button.
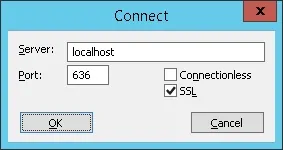
If the system displays an error message, your domain controller is not offering the LDAPS service yet.
To solve this, we are going to install a Windows Certification authority on the next part of this tutorial.
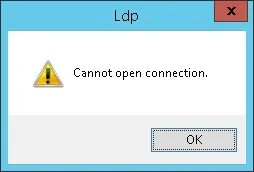
If you were able to successfully connect to the localhost on port 636 using SSL encryption, you may skip the next part of this tutorial.
Tutorial - Certification Authority Installation on Windows
We need to install the Windows certification authority service.
The local certification authority will provide the domain controller with a certificate that will allow the LDAPS service to operate on the TCP port 636.
Open the Server Manager application.
Access the Manage menu and click on Add roles and features.

Access the Server role screen, select the Active Directory Certificate Services and click on the Next button.
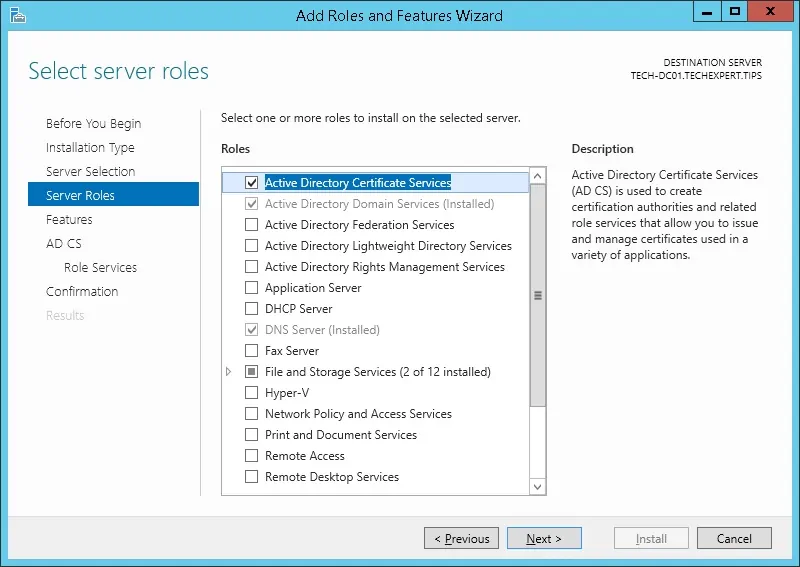
On the following screen, click on the Add features button.
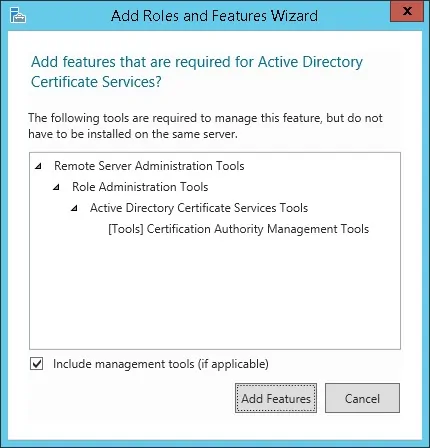
Keep clicking on the Next button until you reach the role service screen.
Enable the option named Certification Authority and click on the Next button.
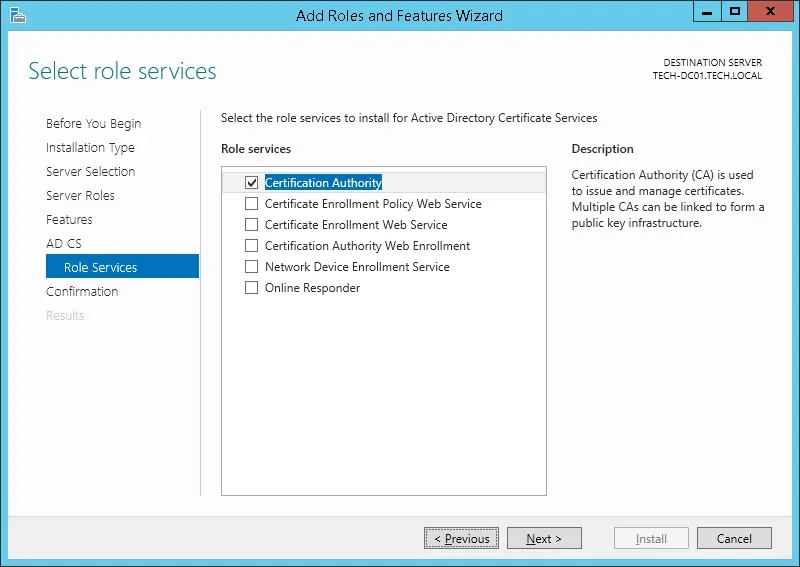
On the confirmation screen, click on the Install button.
Wait the Certification Authority installation to finish.
Open the Server Manager application.
Click on the yellow flag menu and select the option: Configure Active Directory Certificate Services
On the credentials screen, click on the Next button.
Select the Certification Authority option and click on the Next button.
Select the Enterprise CA option and click on the Next button.
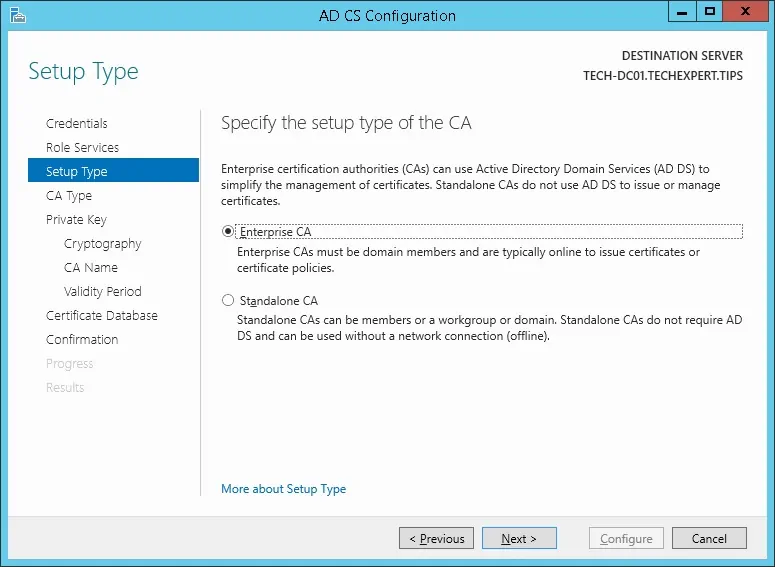
Select the Create a new private key option and click on the Next button.
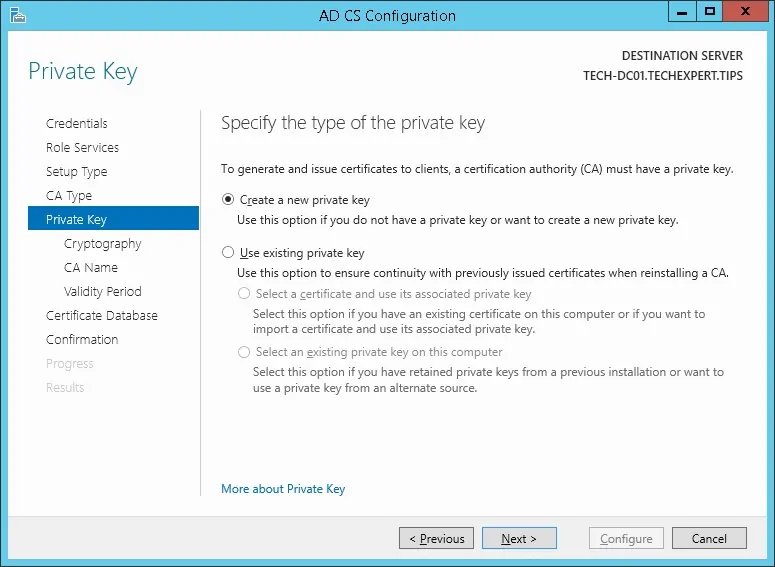
Keep the default cryptography configuration and click on the Next button.
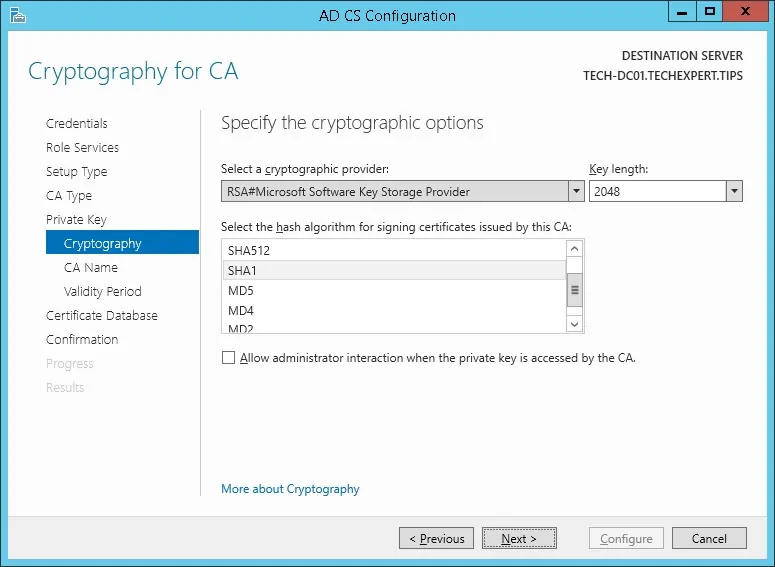
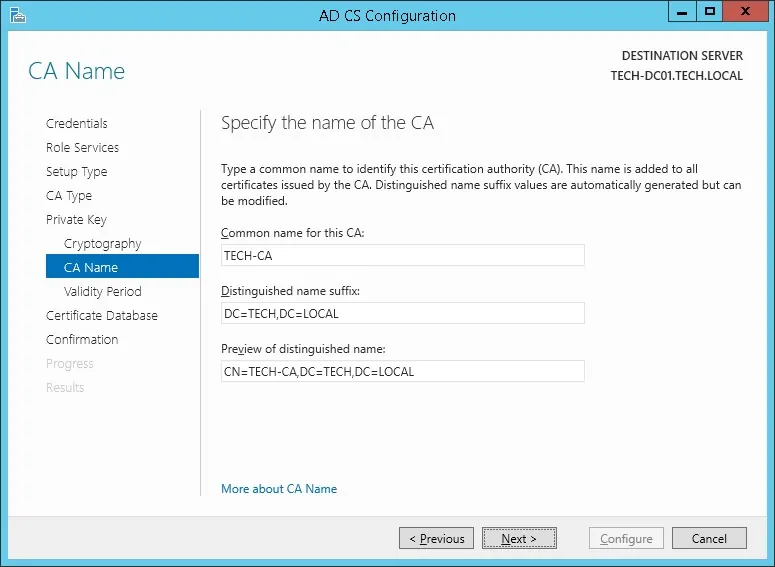
Set a common name to the Certification authority and click on the Next button.
In our example, we set the common name: TECH-CA
Set the Windows Certification authority validity period.
Keep the default Windows Certification authority database location.
Verify the summary and click on the Configure button.
Wait for the Windows server certification authority installation to finish.
After finishing the certification authority installation, reboot your computer.
You have finished the Windows Certification authority installation.
Zabbix - Testing the LDAP over SSL Communication Again
We need to test if your domain controller is offering the LDAP over SSL service on port 636.
After finishing the Certification authority installation, wait 5 minutes and restart your domain controller.
During boot time, your domain controller will automatically request a server certificate from the local certification authority.
After getting the server certificate, your domain controller will start offering the LDAP service over SSL on the 636 port.
On the domain controller, access the start menu and search for the LDP application.

Access the Connection menu and select the Connect option.

Try to connect to the localhost using the TCP port 636.
Select the SSL checkbox and click on the Ok button.

Try to connect to the localhost using the TCP port 636.
Select the SSL checkbox and click on the Ok button.
This time, you should be able to connect to the LDAP service on the localhost port 636.
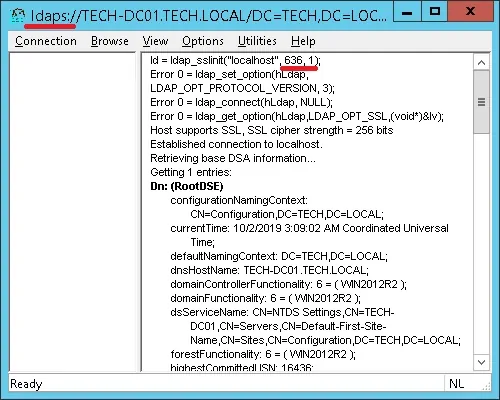
If you are not able to connect to port 636, reboot the computer again and wait 5 minutes more.
It may take sometime before your domain controller receives the certificate requested from the Certification Authority.
Tutorial - Windows Domain Controller Firewall
First, we need to create a Firewall rule on the Windows domain controller.
This firewall rule will allow the Zabbix server to query the Active directory database.
On the domain controller, open the application named Windows Firewall with Advanced Security
Create a new Inbound firewall rule.
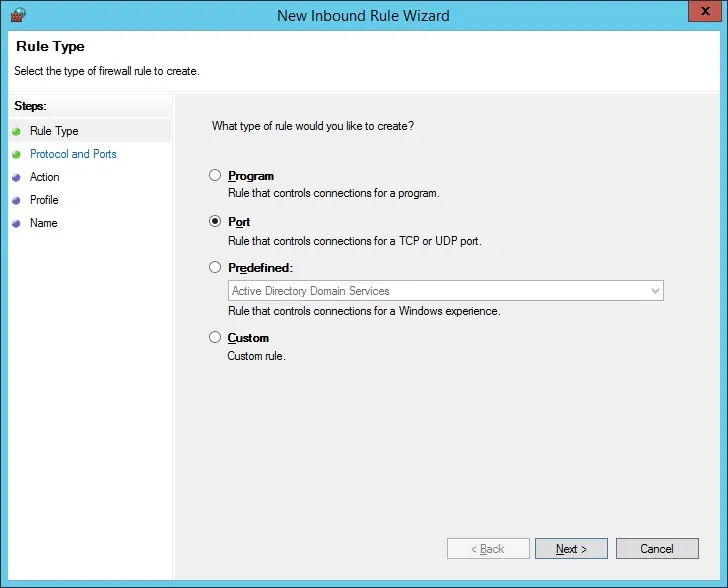
Select the PORT option.
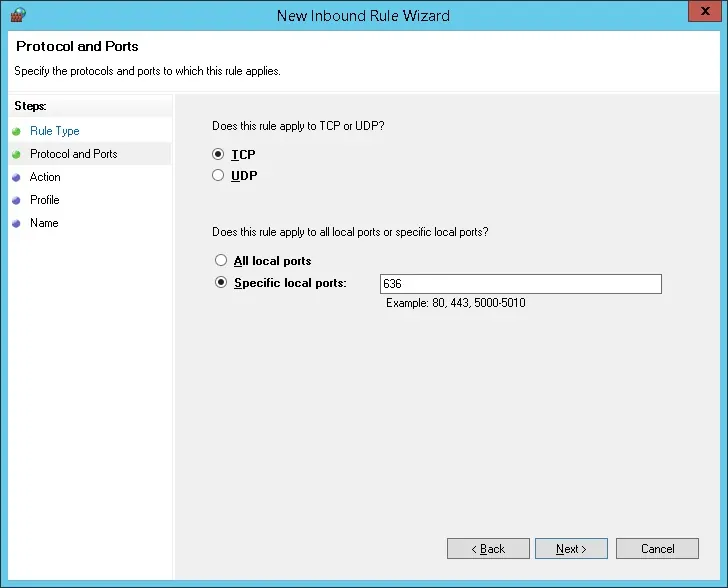
Select the TCP option.
Select the Specific local ports option.
Enter the TCP port 636.
Select the Allow the connection option.
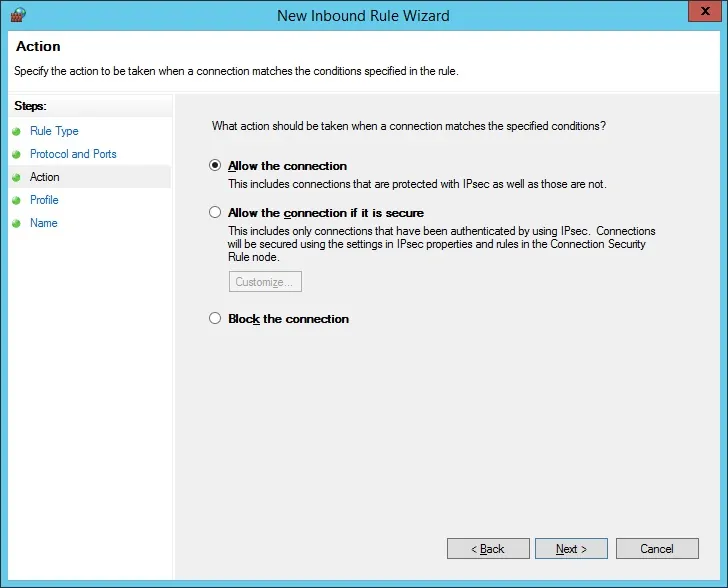
Check the DOMAIN option.
Check the PRIVATE option.
Check the PUBLIC option.
Enter a description to the firewall rule.
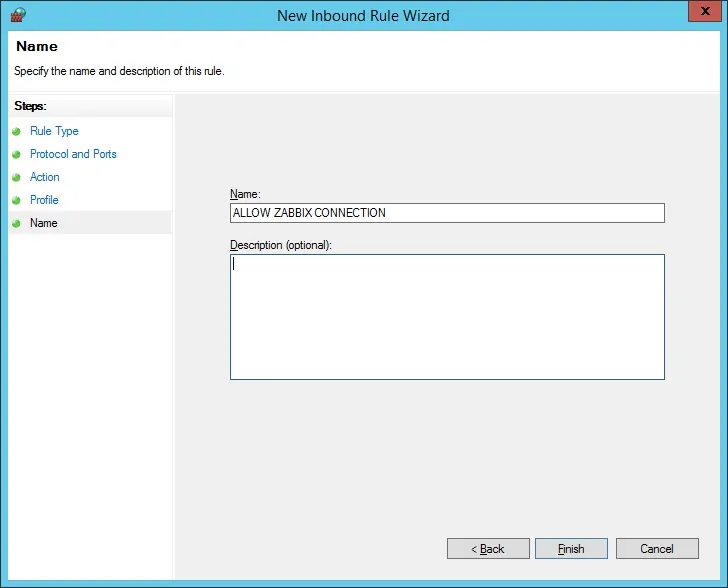
Congratulations, you have created the required firewall rule.
This rule will allow Zabbix to query the Active directory database.
Tutorial - Windows Domain Account Creation
Next, we need to create at least 2 accounts on the Active directory database.
The ADMIN account will be used to login on the Zabbix web interface.
The ZABBIX account will be used to query the Active Directory database.
On the domain controller, open the application named: Active Directory Users and Computers
Create a new account inside the Users container.
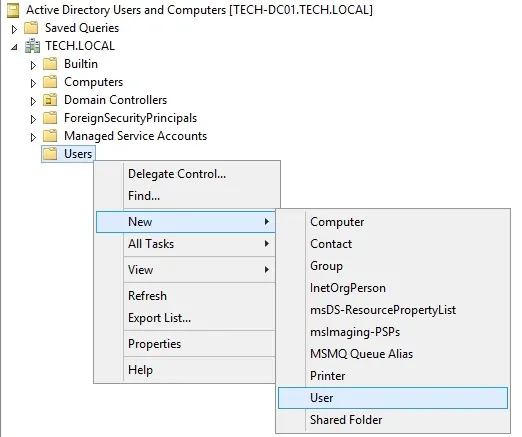
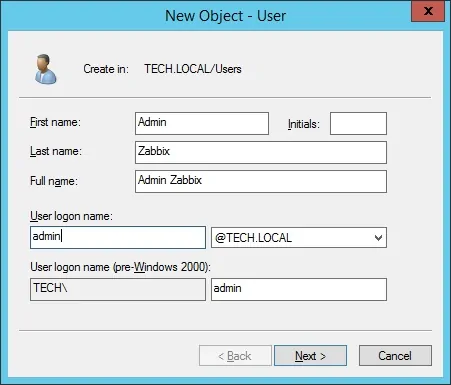
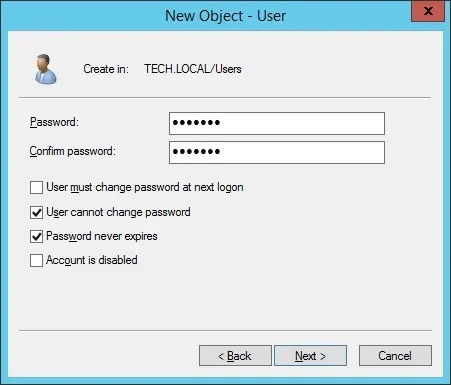
Create a new account named: admin
Password configured to the Admin user: 123qwe.
This account will be used to authenticate as admin on the Zabbix web interface.
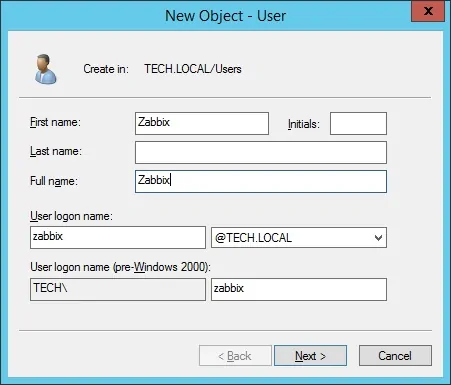
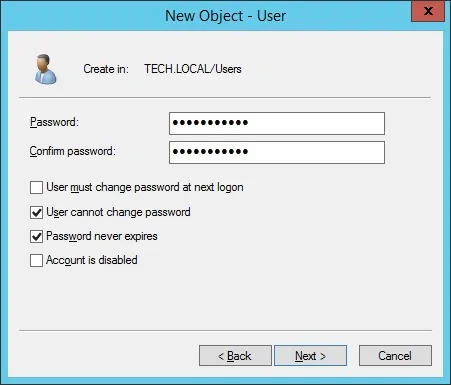
Create a new account named: zabbix
Password configured to the Zabbix user: 123qwe.
This account will be used to query the passwords stored on the Active Directory database.
Congratulations, you have created the required Active Directory accounts.
Tutorial - Preparing the Zabbix LDAPS Communication
On the Zabbix server command-line, edit the ldap.conf configuration file.
Add the following line at the end of the ldap.conf file.
Here is the content of our ldap.conf file.
The Zabbix server must be able to communicate with the domain controller using its DNS name. (FQDN)
To solve this problem, the Zabbix server may use the domain controller as a DNS server to enable the translation of TECH-DC01.TECH.LOCAL to the IP address 192.168.15.10.
If you don't want to set the Windows domain controller as the DNS server of the Zabbix server, you may add a static entry on the hosts file.
Use the PING command to verify if the Zabbix server is able to translate the hostname to IP address.
In our example, the Zabbix server was able to translate the TECH-DC01.TECH.LOCAL hostname to 192.168.15.10 using a static entry on the hosts file.
Use the following command to test the LDAPS communication.
It will try to get a copy of the domain controller certificate.
Keep in mind that you need to change the IP address above to your Domain controller.
The system should display a copy of the Domain Controller certificate.
Configurations! You have finished the required Zabbix command-line configurations.
Tutorial - Zabbix LDAP Authentication on Active Directory
Open your browser and enter the IP address of your web server plus /zabbix.
In our example, the following URL was entered in the Browser:
• http://192.168.15.11/zabbix
On the login screen, use the default username and default password.
• Default Username: Admin
• Default Password: zabbix
After a successful login, you will be sent to the Zabbix Dashboard.
On the dashboard screen, access the Administration menu and select the Authentication option.
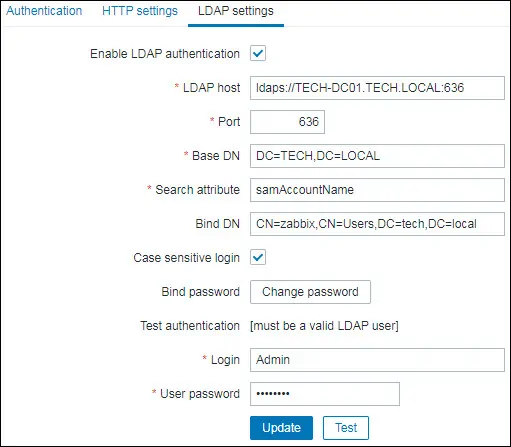
On the Authentication screen, access the LDAP settings tab.
You need to configure the following items:
• LDAP Host: ldaps://TECH-DC01.TECH.LOCALO:636
• Port: 636
• Base DN: dc=tech,dc=local
• Search Attribute: SaMAccountName
• Bind DN: CN=zabbix,CN=Users,DC=tech,DC=local
Enter the Admin username, its password and click on the Test button.
You need to change TECH-DC01.TECH.LOCAL to your domain controller hostname.
You need to change the domain information to reflect your Network environment.
You need to change the bind credentials to reflect your Network environment.
If your test succeeds, you should see the following message.
On the Authentication screen, select the Ldap option to enable the LDAPS authentication on Active Directory.
After finishing your configuration, you should log off the Zabbix web interface.
Try to login using the Admin user and the password from the Active Directory database.
On the login screen, use the Admin user and the password from the Active Directory database.
• Username: Admin
• Password: Enter the Active directory password.

Congratulations! You have configured the Zabbix LDAP authentication on Active Directory using LDAP.
In order to authenticate a user against Active directory, the user account must also exist in the Zabbix server user database.
