Would you like to learn how to perform a Radius Server Installation on Windows 2012? In this tutorial, we are going to show you how to install and configure the Radius service on Windows server.
• Windows 2012 R2
• Network Policy and Access Service
In our example, the Radius server uses the IP address 192.168.0.50.
In our example, a Network Switch uses the IP address 192.168.0.10.
In our example, a Desktop running Windows 10 uses the IP address 192.168.0.20.
Both the Network Switch and the Desktop want to authenticate on the Radius database.
Windows Playlist:
On this page, we offer quick access to a list of videos related to Windows installation.
Don't forget to subscribe to our youtube channel named FKIT.
Windows Related Tutorial:
On this page, we offer quick access to a list of tutorials related to Windows.
Tutorial - Radius Server Installation on Windows
Open the Server Manager application.
Access the Manage menu and click on Add roles and features.
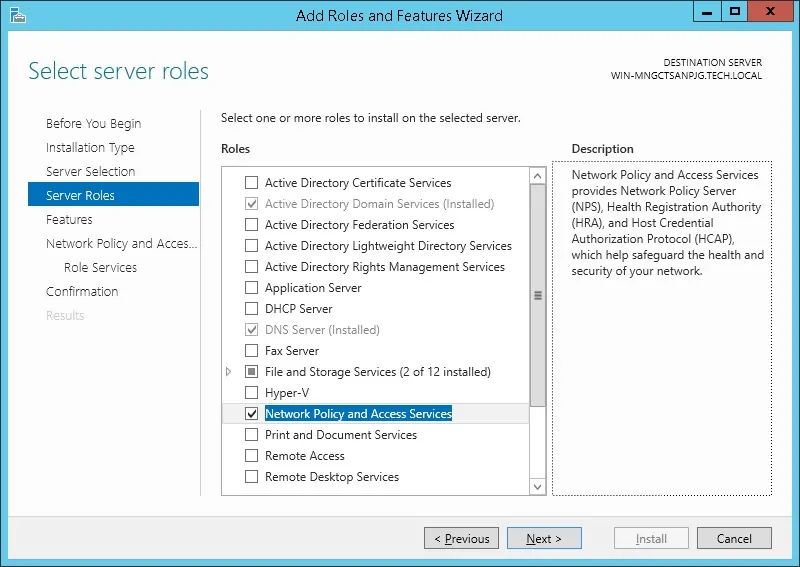
Access the Server roles screen, select the Network Policy and Access Service option.
Click on the Next button.
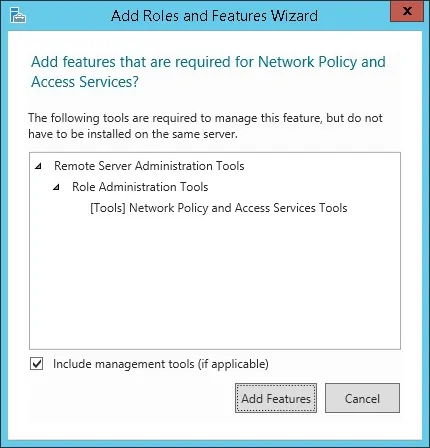
On the following screen, click on the Add features button.
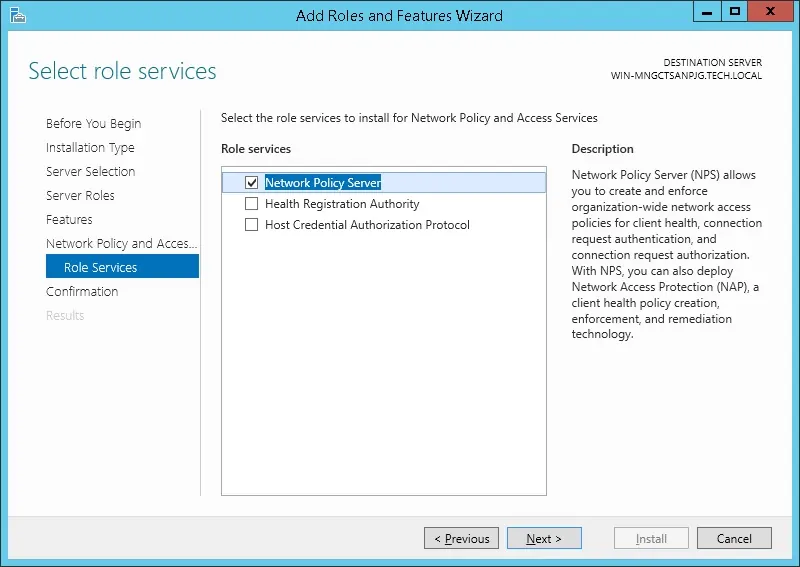
On the Role service screen, click on the Next Button.
On the next screen, click on the Install button.
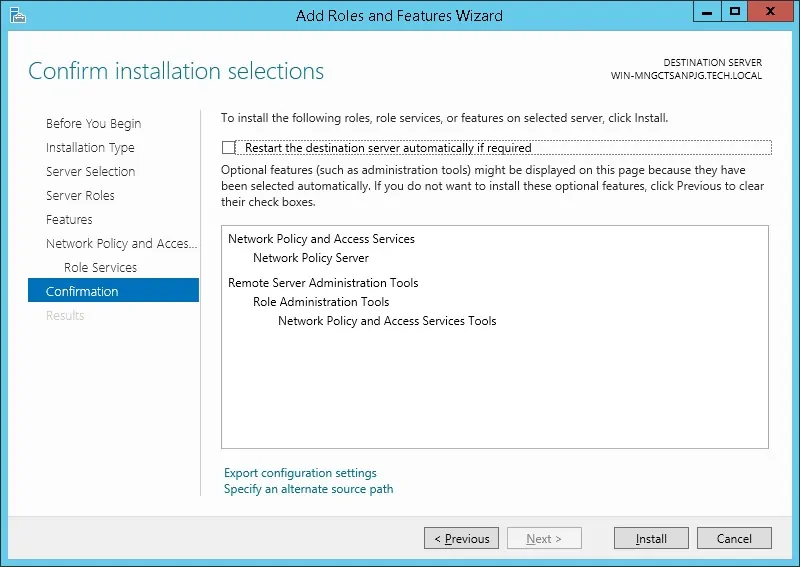
You have finished the Radius server installation on Windows 2012.
Tutorial Radius Server - Active Directory Integration
Next, you need to create a group of authorized users to authenticate using Radius.
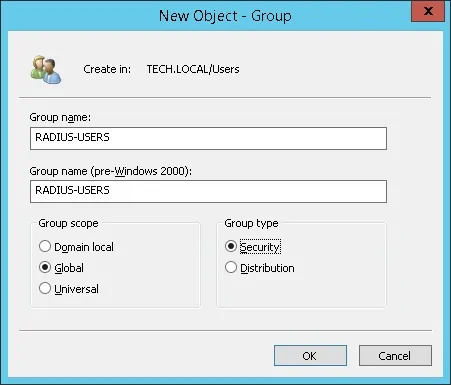
The RADIUS-USERS group will list the user accounts that are allowed to authenticate on the Radius server.
On the domain controller, open the application named: Active Directory Users and Computers
Create a new group inside the Users container.
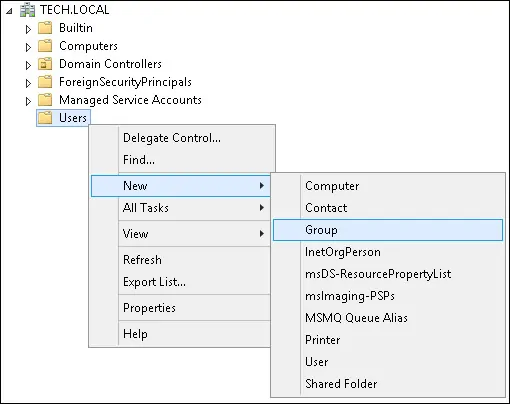
Create a new group named: RADIUS-USERS.
Members of this group will be allowed to authenticate on the Radius server.
We will also create 2 user accounts to test our configuration.
Create a new user account inside the Users container.
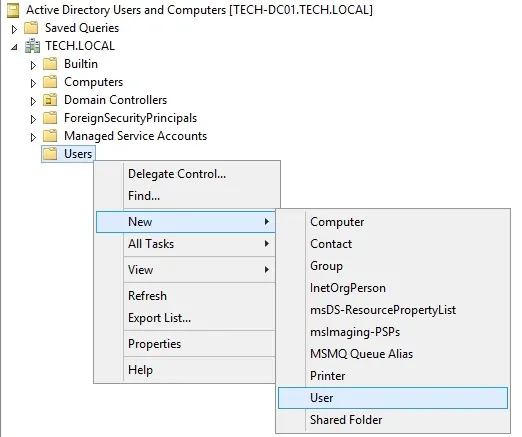
Create a new user account named: VEGETA
The Vegeta user account will be allowed to authenticate on the Radius server.
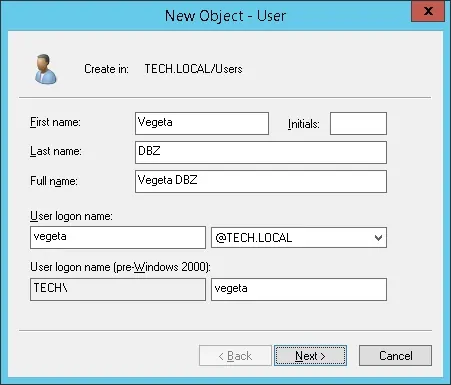
Set the Vegeta user account as a member of the RADIUS-USERS group.
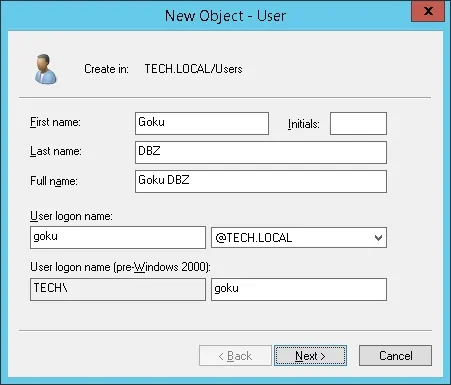
Next, create a new user account named: GOKU
The Goku user account will not be a member of the RADIUS-USERS group.
The Goku user account will not be allowed to authenticate on the Radius server.
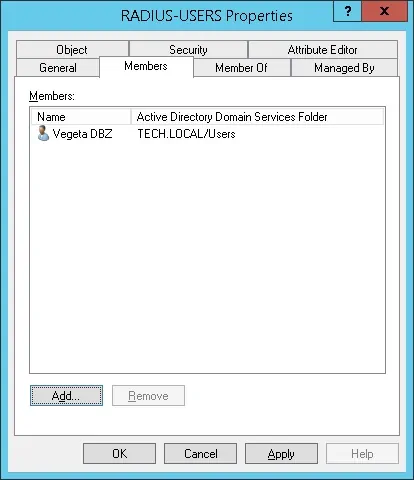
In our example, Members of the RADIUS-USERS are allowed to authenticate on the Radius server.
In our example, the Vegeta user account is a member of the RADIUS-USERS group.
In our example, the Goku user account is not a member of the RADIUS-USERS group.
You have finished the required Active Directory configuration.
Tutorial Radius Server - Add Client Devices
On the Radius server, open the application named: Network Policy Server
You need to authorize the Radius server on the Active directory database.
Right-click on NPS(LOCAL) and select the Register server in Active Directory option.
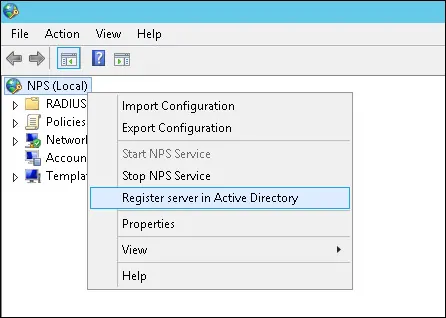
On the confirmation screen, click on the OK button.
Next, you need to configure Radius clients.
Radius clients are devices that will be allowed to request authentication from the Radius server.
Important! Do not confuse Radius clients with Radius users.
Right click on Radius Clients folder and select the New option.
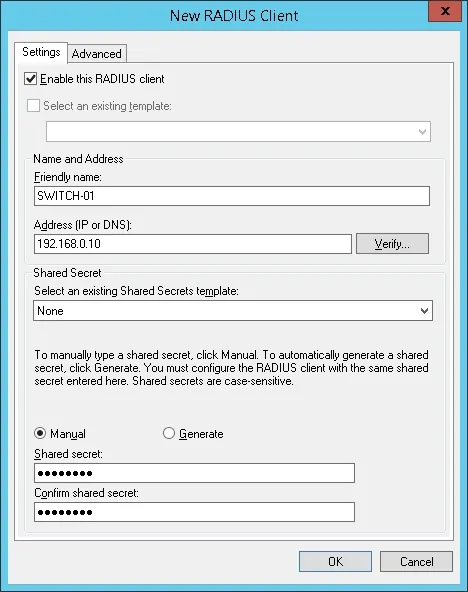
Here is an example of a Client configured to allow a Cisco switch to connect to the Radius server.
You need to set the following configuration:
• Friendly name to the device.
• Device IP Address
• Device Shared secret.
The Shared secret will be used to authorize the device to use the Radius server.
Add another client device, set the IP address of your Desktop and the shared secret kamisma123.
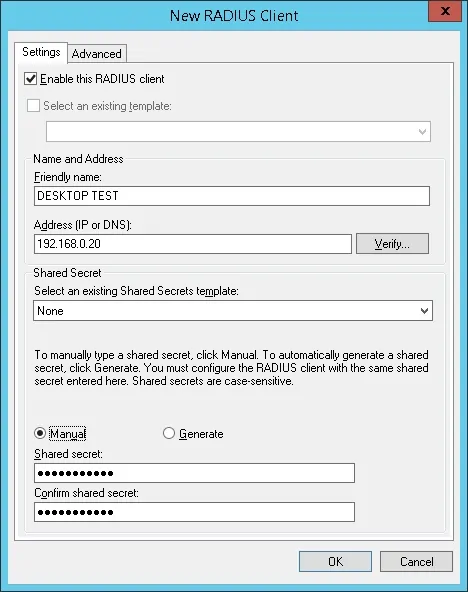
You have finished the Radius client configuration.
Tutorial Radius Server - Configure a Network Policy
Now, you need to create a Network Polity to allow authentication.
Right click on the Network Policies folder and select the New option.
Enter a name to the network policy and click on the Next button.
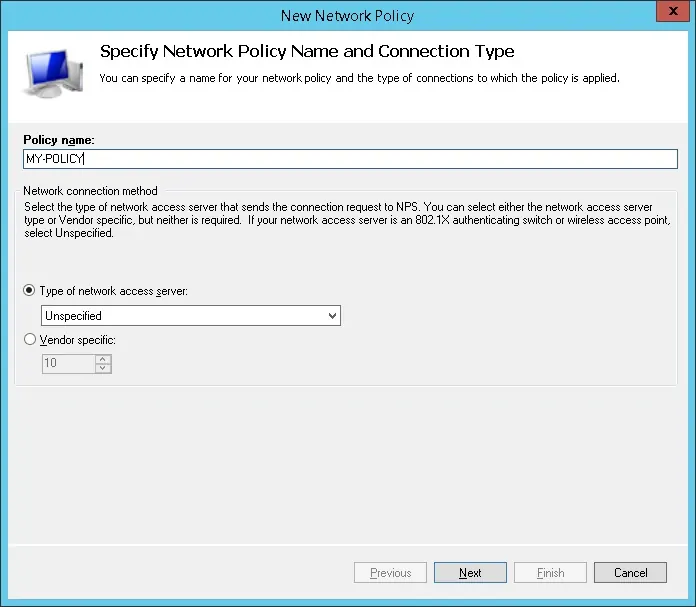
Click on the Add condition button.
We are going to allow members of the RADIUS-SERS group to authenticate.
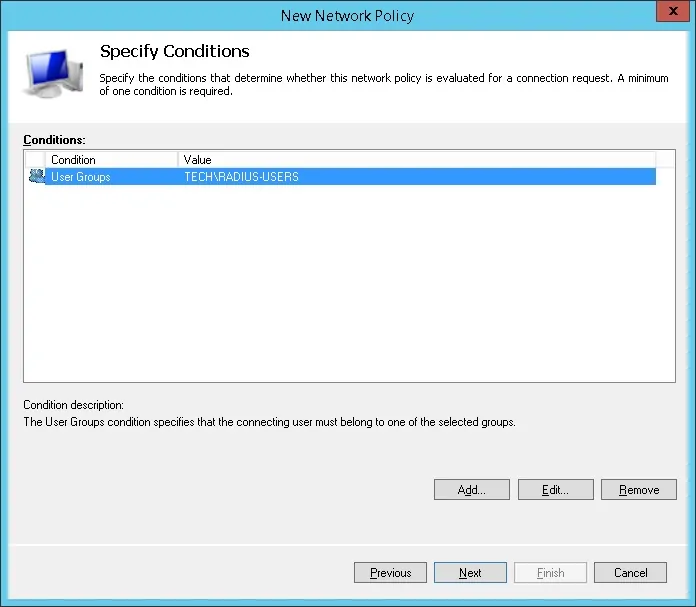
Select the User group option and click on the Add button.
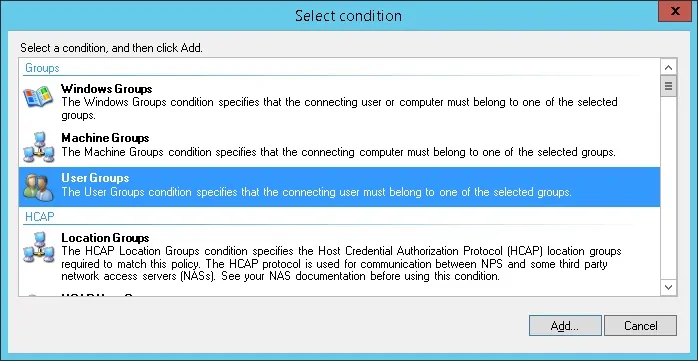
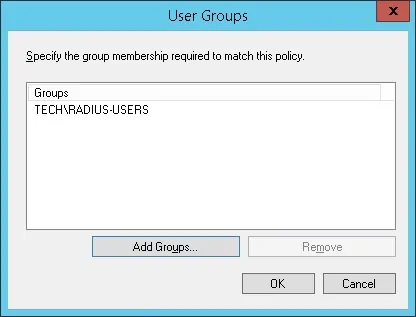
Click on the Add Groups button and locate the RADIUS-USERS group.
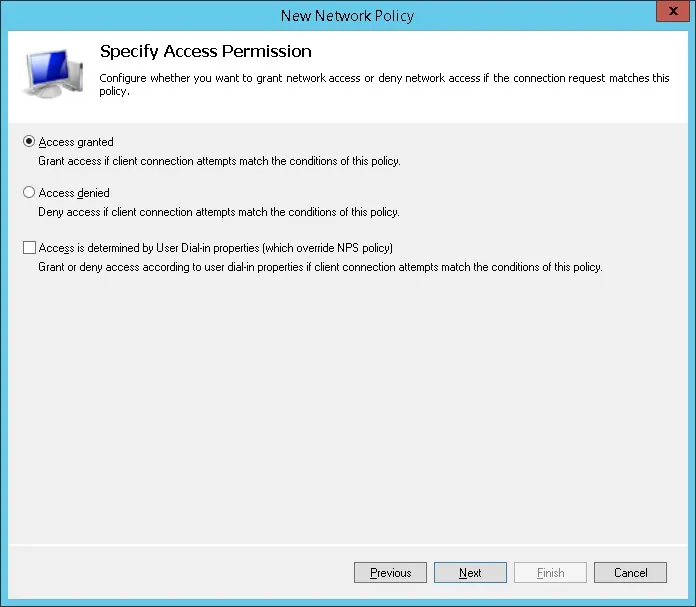
Select the Access granted option and click on the Next button.
This will allow members of the RADIUS-USERS group to authenticate on the Radius server.
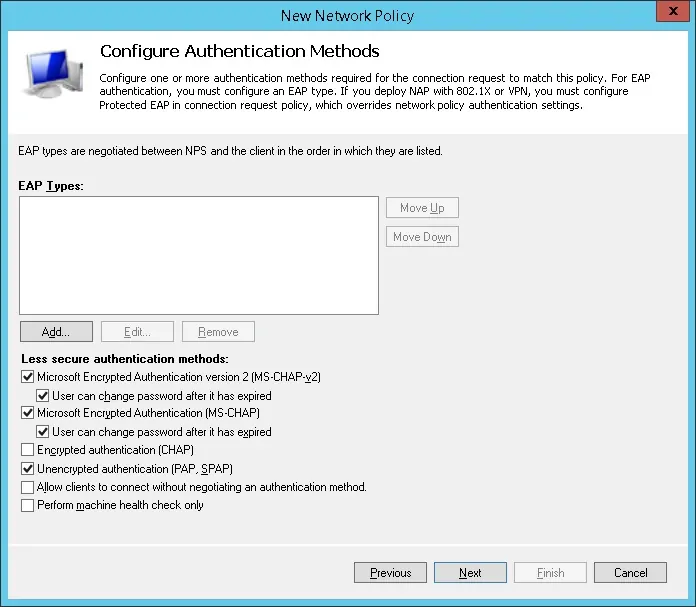
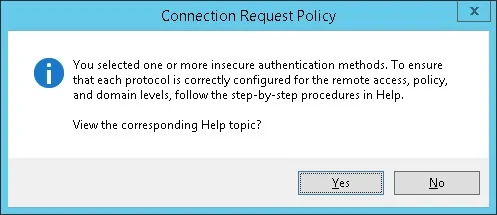
On the Authentication Methods screen, select the Unencrypted authentication (PAP, SPAP) option.
If the following warning is presented, click on the No button.
Verify the Radius server configuration summary and click on the Finish button.
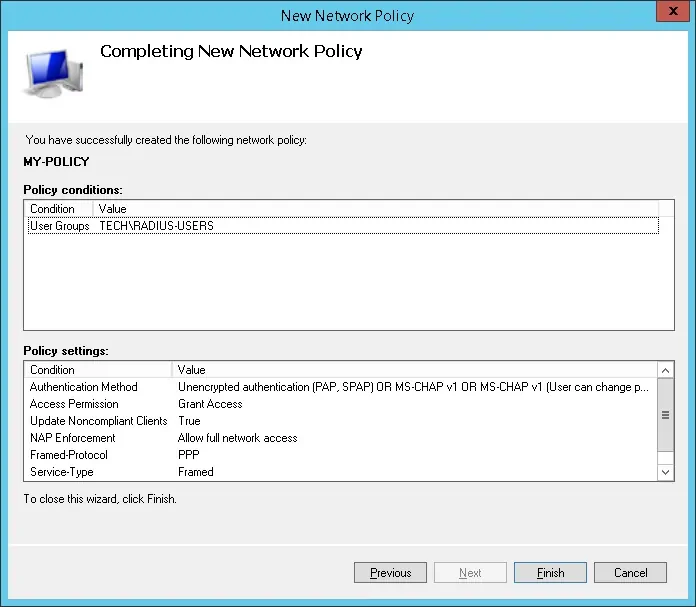
Congratulations! You have finished the Radius server configuration.
Tutorial Radius Server - Authentication Test
Test your radius authentication on your Desktop using the NTRadPing software.
The device running the NTRadPing software must be configured as a Radius client on the Radius server.
Here is a Radius authentication test example.
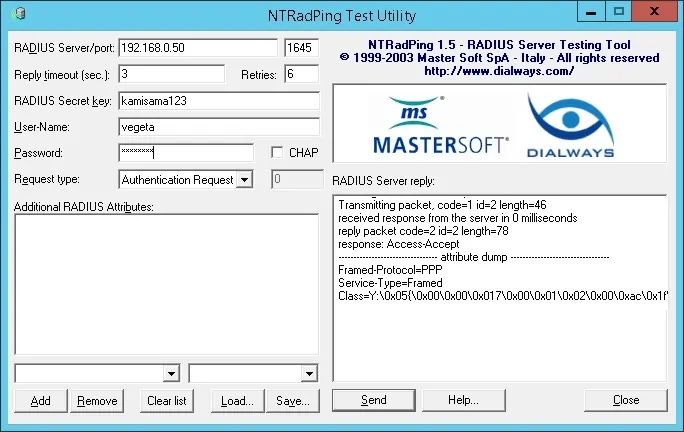
In our example, we used our Desktop as the Radius client device.
In our example, the Vegeta user account was able to authenticate on the Radius server.
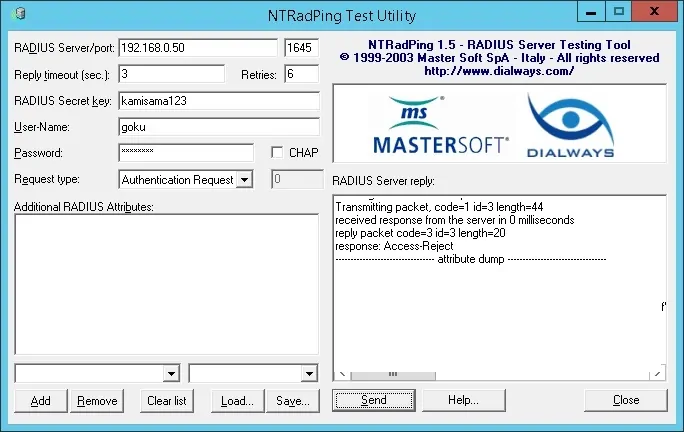
In our example, the Goku user account was not able to authenticate on the Radius server.
The Goku user account is not a member of the RADIUS-USERS group in Active Directory.

Leave A Comment
You must be logged in to post a comment.